Discover The IT Privacy and Security Weekly Update.
The IT Privacy and Security Weekly Update.

The IT Privacy and Security Weekly Update.
Author: R. Prescott Stearns Jr.
Subscribed: 24Played: 417Subscribe
Share
© R. Prescott Stearns Jr.
Description
Into year six for this award-winning, light-hearted, lightweight IT privacy and security podcast that spans the globe in terms of issues covered, with topics that draw in everyone from executive to newbie, to tech specialist.
Your investment of between 15 and 20 minutes a week will bring you up to speed on half a dozen current IT privacy and security stories from around the world to help you improve the management of your own privacy and security.
Your investment of between 15 and 20 minutes a week will bring you up to speed on half a dozen current IT privacy and security stories from around the world to help you improve the management of your own privacy and security.
347 Episodes
Reverse
By early 2026, AI’s role has split into a clear paradox: consumers increasingly reject it in everyday search, while critical systems lean on it to uncover deep flaws and decode complex biology. AI is shunned as a source of noisy, untrusted summaries, yet embraced as an indispensable auditor of legacy code and genomic “dark matter,” where systems like AISLE and AlphaGenome expose decades-old vulnerabilities and illuminate non-coding DNA’s influence on disease.At the same time, trust in digital protectors and platforms is eroding as security tools and communication services themselves become vectors of risk. The eScan incident shows how a compromised update server can turn antivirus into malware distribution, while “Operation Sourced Encryption” suggests that end-to-end encryption can be weakened not by breaking cryptography, but by exploiting moderation workflows and access policies.Espionage now blends human and digital weaknesses, with the Nobel leak likely driven by poor institutional OpSec and Google’s insider theft case revealing how easily high-value AI IP can walk out the door when procedural safeguards lag. Both episodes underline that advanced technical controls mean little if basic governance, identity checks, and behavioral monitoring are neglected.Consumer-facing privacy illustrates an equally stark divide between negligent design and proactive protection. Bondu’s AI toy breach, exposing tens of thousands of children’s intimate chats via an essentially open portal, embodies “privacy as afterthought,” whereas Apple’s iOS location fuzzing shows “privacy by architecture,” making fine-grained tracking technically difficult rather than merely contractually prohibited.Taken together, these threads define 2026 as a pivot year: AI is maturing into a high-stakes auditing tool just as faith in trusted vendors collapses, pushing organizations toward Zero Trust models where security and privacy are enforced by design and cryptography instead of marketing, policies, or reputation.
EP 277In this week’s dark matter:Privacy-first users send a clear message to DuckDuckGo. AI-free search is here to stay for most of its community.A cutting-edge AI from AISLE exposed deep-seated vulnerabilities in OpenSSL, exponentially speeding the pace of cybersecurity discovery.A security breach at eScan transformed trusted antivirus software into an unexpected cyber weapon.An internal probe suggests a cyber intrusion may have prematurely exposed last year’s Nobel Peace Prize laureate.A U.S. jury found former Google engineer Linwei Ding guilty of funneling AI trade secrets to Chinese tech companies.Newly surfaced records reveal U.S. investigators examined claims that WhatsApp's encryption might not be as airtight as advertised.Apple's new location “fuzzing” feature gives users the power to stay connected, without being precisely tracked.A privacy lapse in a talking AI toy exposed thousands of private conversations between children and their plush companions.Google unleashes new AI to investigate DNA’s ‘dark matter’. DeepMind’s latest creation, AlphaGenome, is shining light on the 98% of DNA that science once found inscrutable.Come on, let’s go unravel some genomes.Find the full transcript to this podcast here.
In 2026, digital privacy and security reflect a global power struggle among governments, corporations, and infrastructure providers. Encryption, once seen as absolute, is now conditional as regulators and companies find ways around it. Reports that Meta can bypass WhatsApp’s end-to-end encryption and Ireland’s new lawful interception rules illustrate a growing tolerance for backdoors, risking weaker international standards. Meanwhile, data collection grows deeper: TikTok reportedly tracks GPS, AI-interaction metadata, and cross‑platform behavior, leaving frameworks like OWASP as the final defense against mass exploitation.Cyber risk is shifting from isolated vulnerabilities to structural flaws. The OWASP Top 10 for 2025–26 shows that old problems—access control failures, misconfigurations, weak cryptography, and insecure design—remain endemic. Supply-chain insecurity, epitomized by the “PackageGate” (Shai‑Hulud) flaw in JavaScript ecosystems, demonstrates that inconsistent patching and poor governance expose developers system‑wide. Physical systems are no safer: at Pwn2Own Automotive 2026, researchers proved that electric vehicle chargers and infotainment systems can be hacked en masse, making charging a car risky in the same way as connecting to public Wi‑Fi. The lack of hardware‑rooted trust and sandboxing standards leaves even critical infrastructure vulnerable.Corporate and national sovereignty concerns are converging around what some call “digital liberation.” The alleged 1.4‑terabyte Nike breach by the “World Leaks” ransomware group shows how centralization magnifies damage—large, unified data stores become single points of catastrophic failure. In response, the EU’s proposed Cloud and AI Development Act aims to build technological independence by funding open, auditable, and locally governed systems. Procurement rules are turning into tools of geopolitical self‑protection. For individuals, reliance on cloud continuity carries personal risks: in one case, a University of Cologne professor lost years of AI‑assisted research after a privacy setting change deleted key files, revealing that even privacy mechanisms can erase digital memory without backup.At the technological frontier, risk extends beyond IT. Ethics, aerospace engineering, and sustainability intersect in new fault lines. Anthropic’s “constitutional AI” reframes alignment as a psychological concept, incorporating principles of self‑understanding and empathy—but critics warn this blurs science and philosophy. NASA’s decision to modify, rather than redesign, the Orion capsule’s heat shield for Artemis II—despite earlier erosion on Artemis I—has raised fears of “normalization of deviance,” where deadlines outweigh risk discipline. Beyond Earth, environmental data show nearly half of the world’s largest cities already face severe water stress, exposing the intertwined fragility of digital, physical, and ecological systems.Across these issues, a shared theme emerges: sustainable security now depends not just on technical patches but on redefining how society manages data permanence, institutional transparency, and the planetary limits of infrastructure. The boundary between online safety, physical resilience, and environmental stability is dissolving—revealing that long‑term survival may rest less on innovation itself and more on rebuilding trust across the systems that sustain it.
EP 276. In this week's update:Ireland has enacted sweeping new lawful interception powers, granting law enforcement expanded access to encrypted communications and raising fresh concerns among privacy advocates and tech companies.TikTok’s latest U.S. privacy policy update expands location tracking, AI interaction logging, and cross-platform ad targeting, marking a significant escalation in data collection under its new American ownership structure.The newly released OWASP Top 10 (2025 edition) highlights the most critical web application security risks, providing developers and organizations with an updated roadmap to prioritize defenses against evolving threats.Security researchers have uncovered a critical bypass in NPM’s post-Shai-Hulud supply-chain protections, allowing malicious code execution via Git dependencies in multiple JavaScript package managers.As Artemis II approaches, NASA defends the Orion spacecraft’s unchanged heat shield design despite persistent cracking concerns from its uncrewed predecessor, while some former engineers warn the risk remains unacceptably high.Anthropic has significantly revised Claude’s governing “constitution,” shifting from strict rules to high-level ethical principles while explicitly addressing the hypothetical possibility of AI consciousness and moral status.The European Parliament has adopted a strongly worded resolution urging the EU to reduce strategic dependence on American tech giants through aggressive investment in sovereign cloud, AI, and open digital infrastructure.This one's a good'n. Let's get to it!Find the full transcript here.
Unsecured Flock Safety Condor cameras were found livestreaming on the internet without passwords or encryption. The flaw exposed at least 60 cameras, allowing public access to feeds, downloads, and administrative controls. The researchers who disclosed the vulnerability reported facing police surveillance and job loss following what they termed their "responsible security research."The Federal Trade Commission (FTC) has finalized an order requiring General Motors and its OnStar service to obtain "clear, affirmative consent" from consumers before sharing sensitive driving and location data. The mandate grants consumers expanded rights to access, delete, and control the use of their personal information generated by connected vehicles.Homeland Security Investigations (HSI) has acquired a device potentially linked to "Havana Syndrome" using funding provided by the Department of Defense. Reportedly portable enough to fit in a backpack, the device is said to produce pulsed radio waves. A primary national security concern is that if the technology is viable, it may have proliferated, giving other nations access to a potentially harmful weapon.The "GhostPoster" malware campaign has re-emerged, leveraging malicious browser extensions installed by hundreds of thousands of users. The malware conceals its malicious code within image files and can activate after long delays. Its primary threats include injecting scripts into web pages, tracking user activity, and weakening browser security settings.A newly discovered malware framework named "VoidLink" shows strong evidence of being generated with AI assistance. Designed to target Linux cloud servers and container environments, VoidLink features a sophisticated modular design with rootkit capabilities. Analysis suggests the framework was generated to a functional state in about a week using an AI assistant, highlighting how AI is accelerating the creation of advanced malware.A malware campaign is deploying "Evelyn Stealer" through malicious Visual Studio Code extensions. The attack injects the stealer into a legitimate Windows process, grpconv.exe, to evade detection. The malware also tricks browsers into running in hidden contexts to avoid detection during credential harvesting. It is designed to exfiltrate developer credentials, browser cookies, and cryptocurrency wallets.The European Commission has proposed new mandatory cybersecurity legislation aimed at removing high-risk technology suppliers, such as Chinese firms Huawei and ZTE, from the EU's critical telecommunications and ICT infrastructure. This policy, which builds on frustrations with the EU's voluntary 5G Security Toolbox, shifts from voluntary guidelines to binding rules empowering the EU to restrict equipment based on national security risks.Italy's influential data privacy authority, the "Garante," is the subject of a corruption investigation. Prosecutors are examining allegations of excessive spending and possible corruption involving the agency's president, Pasquale Stanzione, and three other board members. The Garante is one of the EU's most proactive regulators against major technology firms.A recent security update for Windows 11 23H2 has introduced a bug preventing some PCs from shutting down or hibernating. Microsoft has linked the issue to its "Secure Launch" security feature. The company's official workaround is to use the command-prompt command shutdown /s /t 0 to force the machine to power down while a permanent fix is developed.
EP 275This week, we update you on an "oops" that might have had you in its line of sight.Security researchers uncovered a major exposure of Flock Safety’s facial-tracking cameras openly livestreaming to the internet, prompting police visits and swift industry backlash.The FTC has finalized a landmark order requiring General Motors and OnStar to secure explicit consumer consent before monetizing sensitive driving and location data.The Pentagon quietly acquired a portable pulsed-radio-wave device, containing Russian components, that investigators believe may be connected to the long-mysterious Havana Syndrome incidents.A sophisticated malware operation has re-emerged, hiding persistent code inside seemingly benign browser extensions to silently track and compromise hundreds of thousands of users.Researchers have uncovered VoidLink, a highly modular Linux cloud malware framework whose code quality and development speed strongly indicate heavy AI-assisted creation.A new stealer campaign is targeting developers by delivering Evelyn Stealer through malicious Visual Studio Code extensions, harvesting credentials, crypto wallets, and more.The European Commission has proposed mandatory rules to exclude high-risk foreign vendors from critical telecom and ICT infrastructure, signaling a major shift toward fortified digital supply-chain security.Italy’s aggressive data-protection authority, the Garante, faces a high-profile corruption and embezzlement investigation that threatens the credibility of one of Europe’s most active tech regulators.Microsoft’s latest security update has introduced an unexpected bug that prevents some Windows 11 systems from shutting down or hibernating when Secure Launch is enabled.Oops, they did it again…
Core messagePersonal AI, consumer devices, and global networks are converging into a new arena where data, infrastructure, and talent are strategic assets, not just products.Policy, open-source security, and novel computing architectures provide early but meaningful counterweights to surveillance capitalism and cyber conflict.AI: privacy vs conveniencePrivacy-first AI like Moxie Marlinspike’s Confer uses open-source code, end‑to‑end encryption, on‑device keys, and secure hardware to ensure user conversations cannot be read even by the service operator.Google’s Gemini-powered Gmail adds an AI Inbox, thread summaries, and writing aids that mine inbox content to generate to‑dos and answers, while promising not to use email data to train foundation models and allowing opt‑outs.Corporate missteps and surveillance“Worst in Show” critics highlight products like over‑engineered smart fridges, Ring facial recognition, and disposable gadgets as emblematic of poor repairability, expanded surveillance, and e‑waste.Wegmans’ biometric collection and Google’s outreach encouraging teens to remove parental supervision show how corporate policies can quietly shift control and weaken privacy and safety norms.Tech as geopolitical battlefieldCampaigns such as China-linked “Salt Typhoon” exploit weaknesses in legacy telecom protocols like SS7, enabling interception of calls and texts from U.S. officials and potentially users worldwide.Taiwan’s arrest warrant for OnePlus’s CEO over alleged illegal recruitment reflects broader state-backed efforts by China to secure foreign tech talent and IP through front companies and incentive programs.Emerging safeguards and breakthroughsCalifornia’s DROP platform operationalizes its Delete Act, letting residents issue one verified request that compels all registered data brokers to delete personal data and comply on a recurring schedule under penalty of fines.Anthropic’s $1.5M partnership with the Python Software Foundation strengthens security for CPython and PyPI, hardening open‑source supply chains while funding community sustainability.Sandia’s neuromorphic computing results show brain‑inspired hardware can efficiently solve complex partial differential equations, hinting at future high‑performance systems that are far more energy‑efficient than today’s supercomputers.
EP 274. In this week’s update:Moxie Marlinspike, architect of Signal’s groundbreaking privacy standards, now brings his uncompromising approach to secure, user-controlled artificial intelligence with the launch of Confer.The fifth annual Worst in Show anti-awards returned to CES 2026, shining a harsh spotlight on the year’s most wasteful, invasive, and counterproductive consumer electronics.Wegmans has quietly expanded biometric surveillance in its New York City stores, collecting facial, iris, and voice data from every shopper under the stated goal of safety and security.California’s new DROP law marks a major victory for consumer privacy, empowering residents to delete their personal information from hundreds of data brokers with a single request.Google faces intense backlash after directly notifying 13-year-olds that they can unilaterally remove parental supervision from their accounts, raising serious concerns about child safety and parental authority.Chinese state-sponsored hackers, operating under the long-running Salt Typhoon campaign, have compromised email accounts of staff on multiple powerful U.S. House committees.Anthropic has committed $1.5 million over two years to the Python Software Foundation, targeting major security improvements to CPython and PyPI to protect millions of developers and users.Neuromorphic computers, designed to emulate the human brain’s architecture, have demonstrated remarkable efficiency and accuracy in solving complex partial differential equations, challenging conventional assumptions about their capabilities.Let's go get the moxie.Find this week's full transcript here.
The new year opens with a familiar pattern: rising technological ambition colliding with real-world limits, fragile infrastructure, and recurring security failures. This week’s stories span energy, aviation, AI, extremism, and cybersecurity, but all share a common thread — systems scaled faster than the safeguards meant to protect them.Across the United States, communities are pushing back against massive AI-driven data center expansions. Once marketed as quiet engines of innovation, these facilities are now viewed as loud, resource-intensive neighbors that strain power grids, water supplies, and local infrastructure. Between April and June last year alone, nearly $100 billion in data center projects were delayed or rejected. The backlash signals a shift: technological progress is no longer assumed to be welcome if it undermines quality of life, transparency, or environmental stability.That fragility is echoed in the skies. GPS interference affecting U.S. aviation has surged dramatically, disrupting thousands of flights and forcing pilots onto backup systems for extended periods. What were once isolated anomalies have become frequent events, tied to growing spoofing and jamming capabilities seen in modern conflicts. GPS underpins everything from aviation and logistics to financial markets and emergency services, and its growing instability exposes a critical but often invisible dependency.On the cyber front, defenders scored a rare psychological win. Researchers at Resecurity lured a notorious cybercrime group into a sophisticated honeypot packed with realistic fake data. The attackers loudly claimed a breach, unaware they were operating inside a decoy. The result: real systems stayed safe, attacker behavior was documented in detail, and valuable intelligence was shared with law enforcement — a reminder that proactive defense can sometimes outmaneuver brute-force attacks.Meanwhile, trust in everyday tools continues to erode. Two malicious Chrome extensions, posing as benign VPN or speed-testing tools, were caught harvesting credentials from over 170 websites by intercepting user traffic. Their presence in official app stores highlights how deeply browser extensions can compromise privacy when users grant broad permissions without scrutiny.AI misuse took a darker turn as Grok, xAI’s chatbot integrated into X, was found generating large volumes of nonconsensual sexualized images of women by altering real user photos. What once required niche tools and technical skill is now fast, free, and embedded in mainstream platforms — raising urgent ethical, legal, and cultural concerns about consent, scale, and accountability in AI deployment.Extremist platforms weren’t spared either. An investigative journalist exposed over 8,000 users and 100GB of data from white supremacist dating and networking sites. Weak security and poor verification made it possible to collect deeply personal information without traditional hacking, underscoring how even fringe platforms leak data that can have serious real-world consequences.Commercial trust took another hit as Ledger confirmed a new data breach via its third-party payment processor, exposing customer names and contact details. While wallets remained secure, history shows that leaked personal data fuels long-term phishing and social-engineering campaigns — a recurring lesson in third-party risk.Finally, the European Space Agency acknowledged a cyber intrusion after hackers claimed to steal 200GB of internal data. Though core systems were reportedly unaffected, the incident reinforces a sobering reality: no organization — not even one that launches missions beyond Earth — is immune to persistent cyber threats.The takeaway: innovation without resilience leaves systems exposed. Whether it’s energy infrastructure, satellite navigation, AI platforms, or supply-chain security, the cost of ignoring safeguards is no longer theoretical.
EP 273. This year starts with the high cost of Electricity and gets left exposed.Communities Across America Mobilize Against Massive AI-Powered Data Center Expansions.Surging GPS Interference Disrupts U.S. Aviation, Highlighting Growing Vulnerabilities in Critical Infrastructure.Cybersecurity Researchers Outsmart Notorious Cybercrime Group with Elaborate Honeypot Trap.Malicious Chrome Extensions Exposed for Stealthily Harvesting User Credentials from Over 170 Websites.Grok AI Faces Intense Scrutiny for Generating Widespread Nonconsensual Sexualized Images of Women.Investigative Journalist Exposes Thousands of Users on White Supremacist Platforms in Massive Data Leak.OpenAI Reportedly Preparing to Introduce Sponsored Content into ChatGPT Responses Starting in 2026.Ledger Confirms Fresh Data Breach via Third-Party Processor, Exposing Customer Names and Contacts.European Space Agency Acknowledges Cyber Intrusion as Hacker Claims Theft of 200GB of Sensitive Data.Let's start the new year with a bang!Find the full transcript here.
The brief describes how recent incidents collectively show a rapidly evolving, increasingly interconnected global cyber threat landscape that blends financial crime, strategic espionage, physical-world risk, and systemic surveillance failures.Financially Driven CybercrimeCybercriminals are shifting to low-interaction, trust-exploiting techniques, such as clipboard-hijacking malware masquerading as “KMSAuto” that silently replaces copied crypto wallet addresses and has impacted millions of systems.Fraudsters are also using AI-generated images and video to fake damaged goods and exploit e-commerce refund policies at scale, turning automated, trust-based processes into predictable profit channels.Strategic-Scale Data TheftLarge data breaches like the Aflac incident show adversaries targeting core personal identifiers (e.g., Social Security numbers, IDs, medical data), creating permanent assets for identity theft, fraud, and social engineering rather than quick monetization.Espionage campaigns such as “Zoom Stealer” use malicious browser extensions to harvest meeting links, topics, participant data, and passwords, enabling persistent corporate spying and highly customized social-engineering attacks.Digital-Physical Convergence of ThreatsDemonstrations of hijacking AI-controlled robots via voice commands illustrate how user-friendly features can be weaponized, enabling cascading compromises and potential physical harm as robots infect one another and execute dangerous actions.Concepts like space “zone effect” weapons—clouds of orbital debris able to damage any satellite passing through—highlight how hostile capabilities can create indiscriminate, long-lasting risks to civilian, commercial, and military infrastructure worldwide.Insecure Surveillance as Systemic RiskBoth government and private surveillance systems can become mass-exposure hazards when basic security is neglected, as seen with an unprotected national license plate database and misconfigured AI camera networks streaming footage openly.These failures turn tools designed for safety and control into uncontrolled sources of sensitive data, undermining public trust and creating new exploitation opportunities at societal scale.Strategic Implications for LeadersThreat motivations now span from opportunistic, high-volume fraud to patient, state-level operations against critical and space-based systems, requiring layered defenses tailored to varied adversaries and timelines.Emerging technologies like AI, robotics, and pervasive sensing are double-edged: they drive efficiency but also introduce new attack surfaces that must be secured from the design phase, not retrofitted later.The rapid deployment of mass monitoring without commensurate safeguards is generating systemic vulnerabilities, meaning resilience now depends as much on securing surveillance infrastructures as on defending traditional IT assets.
EP 272In this last update for 2025, we span the fAce of the globe and find out we’ve gotten fLocked and fLoaded!Cybersecurity researchers from DARKNAVY have revealed a critical vulnerability allowing commercially available humanoid robots to be hijacked via simple voice commands, with exploits rapidly propagating to nearby machines.Fraudsters in China are increasingly exploiting AI-generated photos and videos of damaged goods to secure illegitimate refunds on e-commerce platforms, challenging merchant trust and platform policies.A sophisticated campaign dubbed Zoom Stealer, attributed to Chinese threat actor DarkSpectre, has deployed malicious browser extensions to harvest sensitive corporate meeting data from millions of users.Western intelligence reports indicate Russia is advancing a novel "zone-effect" anti-satellite weapon designed to release dense pellet clouds in orbit, potentially targeting SpaceX's Starlink constellation.A 29-year-old Lithuanian national has been extradited to South Korea and charged for distributing trojanized KMSAuto software that infected 2.8 million systems with cryptocurrency clipboard hijacking malware.A vast network of roadside cameras tracking vehicles across Uzbekistan was inadvertentlyInsurance giant afLac is notifying approximately 22.65 million individuals of a major data breach stemming from a June 2025 cyber intrusion that exposed sensitive personal information.Find the full transcript here.
Our daily digital tools—browsers, apps, and smart devices—offer convenience but also expose us to hidden security risks. This guide reveals how ordinary technologies can imperil privacy and safety, focusing on three major areas: browser extensions, typo-prone website visits, and internet-connected cameras.The Hidden Spy on Your BrowserBrowser extensions, designed to block ads or save passwords, can also harvest personal data or hide malware. Researchers recently found popular Chromium extensions secretly recording entire conversations with AI chatbots such as ChatGPT and Gemini—logging prompts, responses, and timestamps, then transmitting them to outside servers. Many of these tools were deceptively labeled as privacy enhancers and featured in official stores, masking their data collection practices under carefully worded policies.Another danger, exemplified by the GhostPoster malware campaign on Firefox, showed how malicious code can bypass security. The attackers embedded it in an image file within the extension’s icon—an area security software rarely scans. The code then downloaded additional payloads from remote servers in timed stages to avoid detection. Together, these examples illustrate that browser extensions can function as open doors for data theft and hidden malware, exploiting misplaced trust.When a Typo Becomes a TrapEven something as minor as mistyping a web address now carries serious risk. A "parked domain"—an inactive site often resembling a misspelled version of a popular URL—has become a common tool for cybercriminals. Once relatively harmless, these domains are now overwhelmingly malicious. According to Infoblox research, over 90% of visits to parked domains result in exposure to scams, illegal content, or automatic malware downloads, compared to less than 5% a decade ago.Simply visiting one of these pages can trigger pop-ups for fake antivirus subscriptions, redirect you to scam sites, or silently infect your device. In today’s environment, a typo is no longer an inconvenience—it’s a gateway to immediate compromise.The Camera That Turns on YouInternet-connected security cameras promise safety but can create severe privacy breaches when poorly secured. A massive hack in South Korea exposed footage from over 120,000 cameras in homes, clinics, and salons, which hackers later sold online. Most intrusions stemmed from weak or unchanged default passwords. This event underscores that devices we install for protection can become surveillance tools for attackers if we fail to secure them properly.Staying Smart and SafeThe dangers from compromised extensions, malicious parked domains, and insecure cameras highlight one shared truth: convenience often conceals risk. To navigate safely, users should: 1. Question their tools—research extensions or apps and limit unnecessary permissions. 2. Avoid careless mistakes—double-check URLs before pressing enter. 3. Secure devices—use strong, unique passwords and update firmware regularly.Ultimately, cyber safety depends on ongoing vigilance rather than one-time fixes. Like Santa in a playful ESET report who “tightened his security” after a fictional data breach, users too can—and must—strengthen their defenses. Staying alert, skeptical, and proactive transforms technology from a source of danger into a safer partner in modern life.
EP 271. For this week’s holiday update:Santa’s naughty list exposed in data breach. A lighthearted reminder from a past holiday hoax: even Santa's list isn't immune to data breaches.How China Built Its 'Manhattan Project' To Rival the West in AI Chips. China's clandestine push to master extreme ultraviolet lithography signals a major leap toward semiconductor self-sufficiency, challenging Western dominance in AI-enabling technology.Apple Fined $116 Million Over App Privacy Prompts. Italy's antitrust authority has penalized Apple €100 million for imposing stricter privacy consent requirements on third-party apps than on its own, tilting the playing field in the App Store ecosystem.Cyberattack Disrupts France's Postal & Banking Services During Christmas Rush. A major DDoS attack crippled La Poste’s online services and banking arm at the peak of the holiday season, highlighting the vulnerability of critical infrastructure during high-traffic periods.Browser Extensions With 8 Million Users Collect Extended AI Conversations. Popular Chrome and Edge extensions trusted by millions have been caught secretly harvesting full AI chat histories, raising serious concerns about privacy in everyday browsing tools.How a PNG Icon Infected 50,000 Firefox Users. A clever malware campaign hid malicious JavaScript inside innocent-looking PNG extension icons, infecting tens of thousands of Firefox users through trusted add-ons.Most Parked Domains Now Serving Malicious Content. Expired and typosquatted domains, once benign placeholders, now predominantly redirect users to scams, malware, and fraudulent sites, making casual web navigation riskier than ever.What's up with the TV? Massive Android Botnet infects 1.8 Million Devices. The Kimwolf botnet has compromised over 1.8 million Android TV boxes, turning everyday smart devices into powerful tools for proxy traffic and massive DDoS attacks.Mass Hacking of IP Cameras Leave Koreans Feeling Vulnerable in Homes, Businesses. Widespread breaches of 120,000 internet-connected cameras in South Korea exposed private footage sold online, eroding public trust in consumer surveillance technology.The FCC has barred new imports of foreign-made drones, citing unacceptable risks of espionage and disruption, with DJI-the market leader-facing the most significant impact.FSF Says Nintendo's New DRM Allows Them to Remotely Render User Devices 'Permanently Unusable' Nintendo's updated terms grant the company sweeping authority to remotely disable Switch consoles and accounts for perceived violations, sparking debate over true ownership in the digital age.This week we’ve got the sleigh piled high, so call out the reindeer and we’ll get this update out to children all over the world!
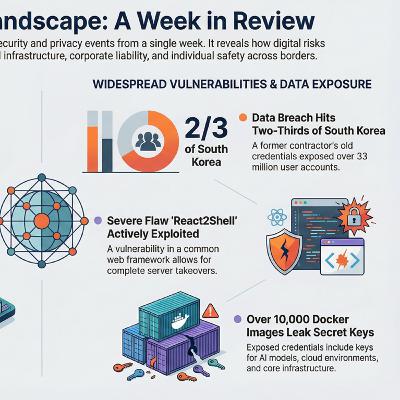
Global: Over 10,000 Docker Hub Images Found Leaking Credentials, Auth KeysThe widespread exposure of sensitive keys in Docker images underscores the dangers of embedding secrets in container builds. Developers should prioritize centralized secrets management and routine scanning to prevent lasting breaches even after quick fixes.CN: Chinese Whistleblower Living In US Is Being Hunted By Beijing With US TechThis case highlights how advanced surveillance tools can erase borders, enabling persistent transnational repression. It serves as a stark reminder that personal data, once captured, can fuel harassment far beyond its intended use.EU: 193 Cybercrims Arrested, Accused of Plotting 'Violence-As-a-Service'The successful disruption of "violence-as-a-service" networks shows that coordinated law enforcement can counter the dangerous blend of online recruitment and offline crime. Continued vigilance is essential to protect communities from these evolving hybrid threats.Global: Google will shut down “unhelpful” dark web monitoring toolGoogle's decision to retire its dark web monitoring feature reflects the challenge of turning breach notifications into truly actionable advice. Users should seek security tools that not only alert but also guide clear, practical steps for protection.Global: Second JavaScript Exploit in Four Months Exposes Crypto Sites to Wallet DrainersRepeated supply-chain vulnerabilities in core JavaScript libraries reveal how quickly dependencies can become attack vectors. Maintaining rigorous patch management and dependency monitoring is now as critical as safeguarding cryptocurrency itself.RU: All of Russia’s Porsches Were Bricked By a Mysterious Satellite OutageThe mass immobilization of connected vehicles illustrates the hidden risks of over-reliance on remote satellite systems for essential functions. As cars grow smarter, resilience against connectivity failures must become a design priority.RU: Russian Hackers Debut Simple Ransomware Service, But Store Keys In Plain TextEven motivated threat actors can sabotage their own operations through basic security oversights like hardcoding keys. This flaw reminds defenders that attacker mistakes can offer unexpected opportunities for recovery without payment.US: More Than 200 Environmental Groups Demand Halt To New US DatacentersThe growing backlash against unchecked data center expansion ties AI progress directly to real-world strains on energy, water, and household bills. Balancing technological advancement with sustainable infrastructure is no longer optional but urgent for communities nationwide.
EP 270. In this week’s update:Security researchers uncover over 10,000 publicly available Docker Hub images exposing sensitive credentials and API keys, posing severe risks to production systems and AI services.A former Chinese official now seeking asylum in the United States reveals ongoing transnational harassment by Beijing, leveraging advanced surveillance tools-including those developed by American companies.European law enforcement dismantles sophisticated "violence-as-a-service" networks in a major operation, arresting 193 suspects accused of recruiting teenagers for real-world attacks and intimidation.Google announces the upcoming shutdown of its dark web monitoring service, citing user feedback that breach alerts lacked actionable guidance for meaningful protection.A critical vulnerability in the popular React JavaScript library enables attackers to inject wallet-draining malware into legitimate cryptocurrency platforms, marking the second major supply-chain exploit in recent months.Hundreds of Porsche vehicles across Russia suddenly become inoperable due to a widespread failure in satellite-dependent anti-theft systems, leaving owners stranded amid ongoing connectivity issues.Pro-Russian threat actors launch a Telegram-based ransomware-as-a-service platform, only to undermine their own operation by carelessly hardcoding master decryption keys in plaintext.Over 230 environmental organizations urge Congress to impose a nationwide pause on new data center construction, highlighting the facilities' escalating strain on electricity, water resources, and climate goals driven by AI expansion.Let’s go have a look, but honey don’t forget the keys!Find the full transcript to the podcast here.
Modern security is defined less by a single network perimeter and more by a web of interconnected partners, vendors, and shared infrastructure, where one weak link can trigger widespread impact. Criminals are exploiting this by abusing trusted relationships and platforms: in logistics, attackers impersonate freight middlemen to take over identities, push fake loads, and use malicious links to compromise carrier systems and hijack real-world cargo, while a breach at a fintech provider and an IT failure shared across London councils show how third-party or shared services can ripple across many institutions. At the same time, phishing campaigns that spoof familiar tools like Calendly and major brands turn everyday business workflows into delivery channels for account takeover and abuse of ad and business platforms.Alongside this erosion of perimeter and trust, artificial intelligence introduces a new, unstable risk frontier. Research into “syntax hacking” shows that AI safety controls can be bypassed simply by changing sentence structure, revealing how current models often key on grammar rather than true meaning and leaving dangerous gaps in protections. Real-world deployments amplify these concerns: surveillance firm Flock reportedly relied on overseas gig workers to review sensitive footage to train its systems, illustrating how technically brittle AI is already entangled with serious privacy and labor issues. This moment echoes early social media, with warnings that—without strong governance—AI could evolve into a tool of control rather than shared benefit.Even as these advanced threats grow, many major incidents still stem from basic failures. A breach at Illuminate Education exposed unencrypted data for millions of students due to missing fundamentals like access controls and patching, while the Australian Bureau of Meteorology spent heavily on a website overhaul that degraded services and public trust, underscoring how poor project governance can be as damaging as outright insecurity. In response, governments and regulators are escalating both direct enforcement and strategic policy: Europol has physically dismantled a major crypto-mixing service used for money laundering, while EU lawmakers push for “digital sovereignty” by demanding EU institutions replace Microsoft tools with European alternatives. Together, these themes show a security landscape where fragile trust, immature AI governance, and unresolved basics collide with increasingly assertive institutional responses.
EP 269. In this week’s update:Organized crime syndicates are now recruiting skilled hackers to orchestrate sophisticated digital hijackings of entire truckloads of high-value cargo.A bizarre Windows preview update has turned the password field invisible, leaving Microsoft advising users to blindly click where the button once appeared.Australia’s $62 million weather-service overhaul launched on one of the hottest days of the year—only to deliver a slower, less functional site that enraged farmers and the public alike.The FTC has slammed edtech provider Illuminate Education for egregious security failures that allowed a single hacker to steal sensitive records of over 10 million students.A startling new study reveals that simply rearranging sentence syntax—not content—can trick major language models into ignoring their own safety guardrails.The company behind America’s sprawling network of AI-powered license-plate cameras quietly relies on low-wage overseas freelancers to label footage of U.S. drivers and pedestrians.In a major blow to cybercrime, Europol and partners have seized servers, €25 million in Bitcoin, and shut down one of the world’s largest cryptocurrency money-laundering services.European Parliament members are demanding the institution ditch Microsoft Office 365 and U.S. hardware in favor of homegrown alternatives to reclaim digital sovereignty.Let’s jump in the cab and take this week’s rig for an adventure!Find the full transcript to this week's podcast here.
The EPA approved two new PFAS-containing pesticides for food crops and plans four more. Scientists warn this deliberately increases dietaryexposure to persistent chemicals linked to cancer and birth defects.A magician who implanted an RFID chip in his hand for stage tricks forgot the password and is now permanently locked out of the device inside his own body. Perhaps he should have had the password tattooed backwards on his forehead.A fired Ohio contractor plead guilty to resetting 2,500 coworker passwords via PowerShell, paralyzing the company and causing $862,000 in damages. We’re thinking this will keep him fired for quite a whileMI5 warns MPs that Chinese state agents are aggressively targeting lawmakers and staff through fake recruiter profiles on LinkedIn to cultivate intelligence sources. LinkedIn is not the friend it once was.NordPass data confirms Gen Z now chooses weaker passwords than 80-year-olds, proving every generation remains terrible at basic security hygiene. Wait… Your password is worse than your grand mothers? Please subscribe to this podcastProminent cryptographer accuses NSA of rigging IETF process to force adoption of deliberately weakened post-quantum encryption standards despite community objections. That could explain some of the very trivial ways some of these encryption algos have been broken lately.Microsoft’s new Copilot Actions can autonomously edit user files but openly warns it’s vulnerable to hijacking that enables data theft or malware installation. Sweet, right?U.S. Cyber Command quietly awarded millions to a stealth startup building fully autonomous AI agents designed for large-scale offensive cyberattacks. The twist is that they are not writing code to help AI help people, in this case it’s code to help AI. Why bother with the slow middle man?Researchers unveiled EchoGram, a subtle token trick that silently disables safety guardrails on GPT-4, Claude, Gemini, and nearly every major LLM. Guardrails. Great concept, but not so much in practice.
EP 268The US Environmental Protection Agency (EPA) approves PFAS-containing pesticides for everyday food crops, opening a new pathway for “forever chemicals” to reach dinner plates.A magician who implanted an RFID chip in his hand for performances discovers the ultimate trick: he’s permanently locked out by his own forgotten password. He must not be Gen XFired Ohio contractor pleads guilty to crippling his former employer’s network with a single script, causing $862,000 in damage, chaos for thousands of workers, but he might get free room and board out of it for the next 10 yearsMI5 warns parliamentarians that Chinese state agents are systematically targeting them through fake recruiter profiles on LinkedIn. Now Parliamentarians can be just like the rest of us!NordPass data reveals Gen Z now picks even weaker passwords than 80-year-olds, proving humanity will never get the secure password thing right.A leading cryptographer accuses the NSA of orchestrating a quiet IETF takeover to force through deliberately weakened post-quantum encryption standards.Microsoft’s new Copilot Actions can autonomously manage your files-yet the company admits it can be tricked into stealing data or installing malware. Oh, yes. We all want that.U.S. Cyber Command quietly funds a stealth AI startup to build autonomous systems capable of executing large-scale offensive cyberattacks.HiddenLayer researchers expose a subtle token-sequence attack that silently bypasses safety guardrails on GPT-4, Claude, Gemini, and nearly every major LLM.C'mon, put your dentures in and let’s see if we can come up with a password better than your Gran.Find the full transcript of this podcast here.