Discover Cybersecurity Tech Brief By HackerNoon
Cybersecurity Tech Brief By HackerNoon

314 Episodes
Reverse
This story was originally published on HackerNoon at: https://hackernoon.com/outlook-vs-gmail-choosing-the-kind-of-email-security-your-business-can-live-with.
Outlook and Gmail are both secure, but built differently. See how control, compliance, and risk management compare for business email in 2025.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #email-security, #it-security, #outlook-vs-gmail-security, #business-email-security, #outlook-vs-gmail-for-business, #microsoft-365-security, #google-workspace-security, #secure-business-email, and more.
This story was written by: @oladapo1. Learn more about this writer by checking @oladapo1's about page,
and for more stories, please visit hackernoon.com.
Both Outlook and Gmail offer strong business email security in 2025, but Outlook favors granular control and compliance, while Gmail prioritizes simplicity and low-maintenance protection.
This story was originally published on HackerNoon at: https://hackernoon.com/beyond-smartphones-motorolas-pivot-to-iot-security-and-smart-home-surveillance.
Examine Motorola’s pivot to IoT security and smart home surveillance. We highlight key features and infrastructure to decode what's important in home safety.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #iot-security, #iot-applications, #mobile, #mobile-app-development, #cybersecurity, #cybercrime, #cyber-threats, #smart-home-surveillance, and more.
This story was written by: @ASmith. Learn more about this writer by checking @ASmith's about page,
and for more stories, please visit hackernoon.com.
Examine Motorola’s pivot to IoT security and smart home surveillance. We highlight key features and infrastructure to decode what's important in home safety.
This story was originally published on HackerNoon at: https://hackernoon.com/the-ddos-of-human-attention-why-curl-killed-its-bug-bounty-and-what-it-means-for-devops.
AI-gen "slop" is killing bug bounties. Learn why cURL shut down its program and how to protect your team from the new DDoS: the flood of low-quality AI noise.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #ai-slop, #devops, #open-source, #bug-bounty, #ddos-of-human-attention, #curl, #command-line-tool, and more.
This story was written by: @omotayojude. Learn more about this writer by checking @omotayojude's about page,
and for more stories, please visit hackernoon.com.
AI-gen "slop" is killing bug bounties. Learn why cURL shut down its program and how to protect your team from the new DDoS: the flood of low-quality AI noise.
This story was originally published on HackerNoon at: https://hackernoon.com/zero-trust-security-in-2026-a-complete-implementation-roadmap-for-ctos.
Zero Trust Security focuses on not believing on any user, any device or anyone even if they are in your network perimeter.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #roadmap, #zero-trust-security, #cto, #2026, #software-development, #zero-trust-security-in-2026, #good-company, and more.
This story was written by: @mahipal.nehra. Learn more about this writer by checking @mahipal.nehra's about page,
and for more stories, please visit hackernoon.com.
Zero Trust Security focuses on not believing on any user, any device or anyone even if they are in your network perimeter. As AI systems become deeply embedded into business workflows, organizations must rethink how they protect sensitive data and automated decision pipelines.
This story was originally published on HackerNoon at: https://hackernoon.com/understanding-testing-vs-evaluation-in-ai-systems.
The distinction between testing and evaluation in AI systems
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #ai-security, #ai-agent, #ai-systems, #ai-red-teaming, #artificial-intelligence, #testing-ai-systems, #security-testing, #best-testing-practices, and more.
This story was written by: @lab42ai. Learn more about this writer by checking @lab42ai's about page,
and for more stories, please visit hackernoon.com.
AI systems introduce complexity: behaviors emerge from training rather than explicit programming. Many companies and organizations building AI systems, especially AI agents, run into problems. They focus heavily on evaluations while neglecting systematic testing.
This story was originally published on HackerNoon at: https://hackernoon.com/owasp-top-10-the-security-stuff-you-keep-meaning-to-learn.
A practical, plain-English guide to the OWASP Top 10—what they mean, how they show up in real apps, and where to start fixing them.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #web-security, #owasp, #owasp-top-10, #broken-access-control, #security-misconfiguration, #server-side-request-forgery, #injection-attacks, #insecure-application-design, and more.
This story was written by: @anjali002. Learn more about this writer by checking @anjali002's about page,
and for more stories, please visit hackernoon.com.
OWASP is a nonprofit that publishes a Top 10 list of security breaches. The list reflects what's actually hurting organizations right now. Broken access control is at the top for a reason. Insecure design is the problem.
This story was originally published on HackerNoon at: https://hackernoon.com/a-class-for-mom-part-2-cybersecurity.
This is a cybersecurity class for senior citizens.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #education, #senior-wisdom, #learning, #online-learning, and more.
This story was written by: @turbulence. Learn more about this writer by checking @turbulence's about page,
and for more stories, please visit hackernoon.com.
This is a cybersecurity class for senior citizens.
This story was originally published on HackerNoon at: https://hackernoon.com/inside-brevity-ai-the-architecture-powering-real-time-hipaa-compliant-clinical-documentation.
Brevity AI’s CTO architected a HIPAA-compliant platform using real-time AI to transform clinical documentation and visit prep at scale.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #hipaa-compliant-documentation, #healthcare-ai-system, #healthcare-nlp-clinical-notes, #secure-healthcare-data, #medical-documentation, #healthcare-ai-architecture, #medical-transcription-platform, #good-company, and more.
This story was written by: @sanya_kapoor. Learn more about this writer by checking @sanya_kapoor's about page,
and for more stories, please visit hackernoon.com.
Brevity AI’s clinical documentation platform compresses hours of chart review and note-taking into minutes through real-time, HIPAA-compliant AI. Architected end-to-end by CTO Purv Rakeshkumar Chauhan, the system combines scalable microservices, medical NLP, secure data infrastructure, and real-time transcription to improve clinician efficiency, accuracy, and patient care.
This story was originally published on HackerNoon at: https://hackernoon.com/how-you-can-test-your-kids-smart-toys-for-privacy.
Are those toys secure? And precisely what data is being handed over when a kid is using these toys?
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #privacy, #kids-safety, #children-privacy, #children-data-safety, #kids-toys-privacy, #the-markup, #bluetooth-toys, #hackernoon-top-story, and more.
This story was written by: @TheMarkup. Learn more about this writer by checking @TheMarkup's about page,
and for more stories, please visit hackernoon.com.
The Markup is looking into what other toys collect private data on your children. A Wi-Fi-enabled toy will likely communicate with your wireless router. A Bluetooth toy will send data to another smart device, such as a smartphone. We’re here to help.
This story was originally published on HackerNoon at: https://hackernoon.com/new-research-shows-64percent-of-third-party-applications-access-sensitive-data-without-authorization.
64% of third‑party applications access sensitive data without legitimate business justification. Google Tag Manager (8%), Shopify (5%), and Facebook Pixel (4%)
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #reflectiz, #cybernewswire, #press-release, #cyber-threats, #cyber-security-awareness, #cybersecurity-tips, #good-company, and more.
This story was written by: @cybernewswire. Learn more about this writer by checking @cybernewswire's about page,
and for more stories, please visit hackernoon.com.
Reflectiz releases its 2026 State of Web Exposure Research. 64% of third‑party applications access sensitive data without legitimate business justification. Google Tag Manager (8%), Shopify (5%), and Facebook Pixel (4%) are top drivers of sensitive data exposure.
This story was originally published on HackerNoon at: https://hackernoon.com/essential-cybersecurity-measures-every-modern-business-should-take.
No business can remove all cyber risk, but every business can make smart moves that reduce it.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity-tips, #business-intelligence, #cyber-threats, #cyber-security-awareness, #cyber-attack, #cybersecurity, #essential-cybersecurity, #startup, and more.
This story was written by: @setudeora. Learn more about this writer by checking @setudeora's about page,
and for more stories, please visit hackernoon.com.
No business can remove all cyber risk, but every business can make smart moves that reduce it.
This story was originally published on HackerNoon at: https://hackernoon.com/airlock-digital-announces-independent-tei-study-quantifying-measurable-roi-and-security-impact.
The study noted that a single security analyst can effectively manage Airlock digital policies in much less time than traditional solutions require.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #cybernewswire, #press-release, #cyber-security-awareness, #cyber-threats, #cybercrime, #cyberattacks, #good-company, and more.
This story was written by: @cybernewswire. Learn more about this writer by checking @cybernewswire's about page,
and for more stories, please visit hackernoon.com.
Airlock Digital's allowlisting solution provides a 224% return on investment (ROI) and a $3.8 million net present value (NPV) over three years for organizations adopting Airlock Digital’s approach. The study noted that a single security analyst can effectively manage Airlock digital policies in much less time than traditional solutions require.
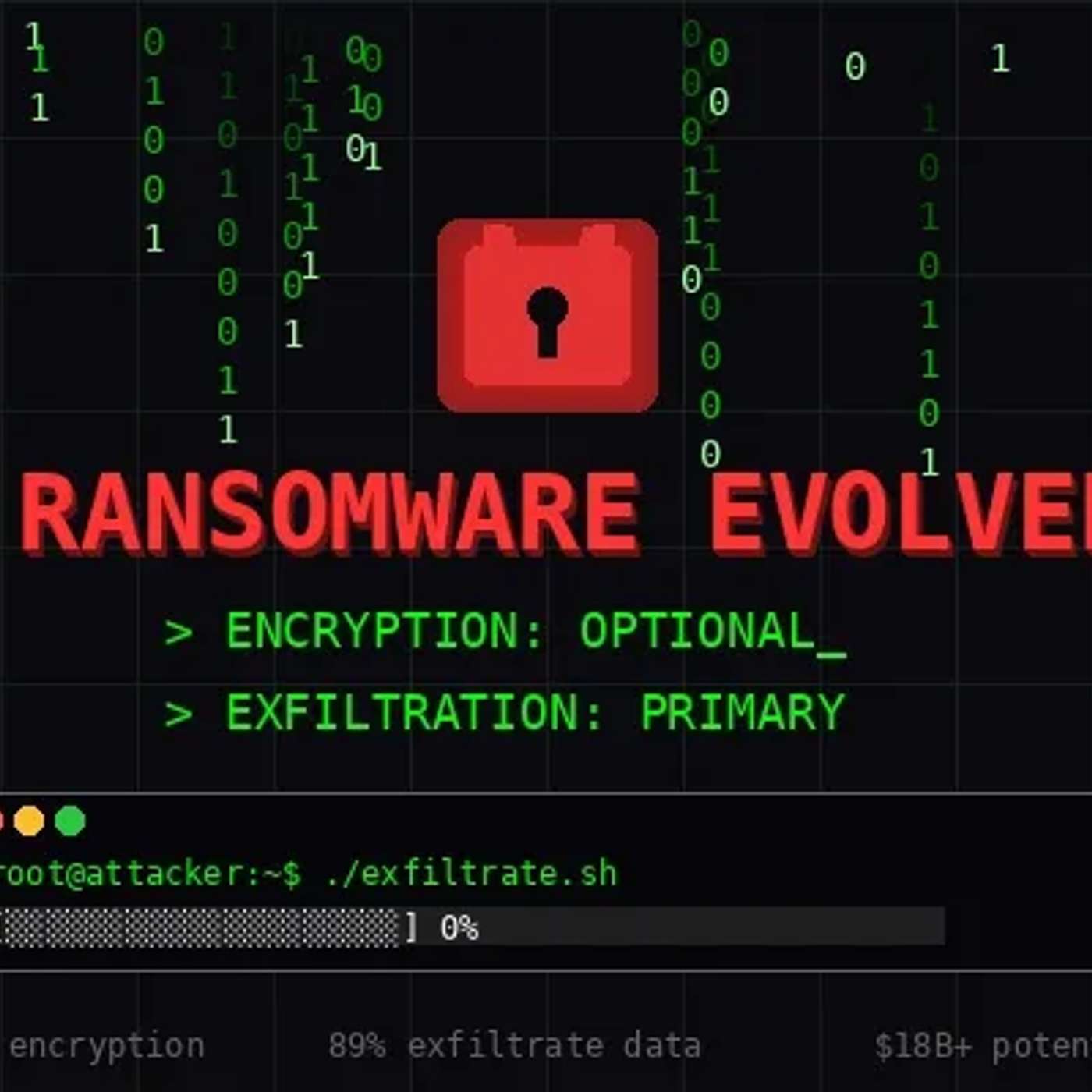
This story was originally published on HackerNoon at: https://hackernoon.com/ransomware-doesnt-need-to-lock-your-files-anymore-heres-why-thats-terrifying.
Ransomware is evolving from "lock your files and demand payment" to "steal everything and threaten to leak it."
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #ransomware, #infosec, #hacking, #data-breach, #cybersecurity-threats, #crypto-threats, #internet-threats, and more.
This story was written by: @anjali002. Learn more about this writer by checking @anjali002's about page,
and for more stories, please visit hackernoon.com.
Ransomware is evolving from "lock your files and demand payment" to "steal everything and threaten to leak it." About 50% of attacks now skip encryption entirely. Payments are declining, but the damage is worse than ever.
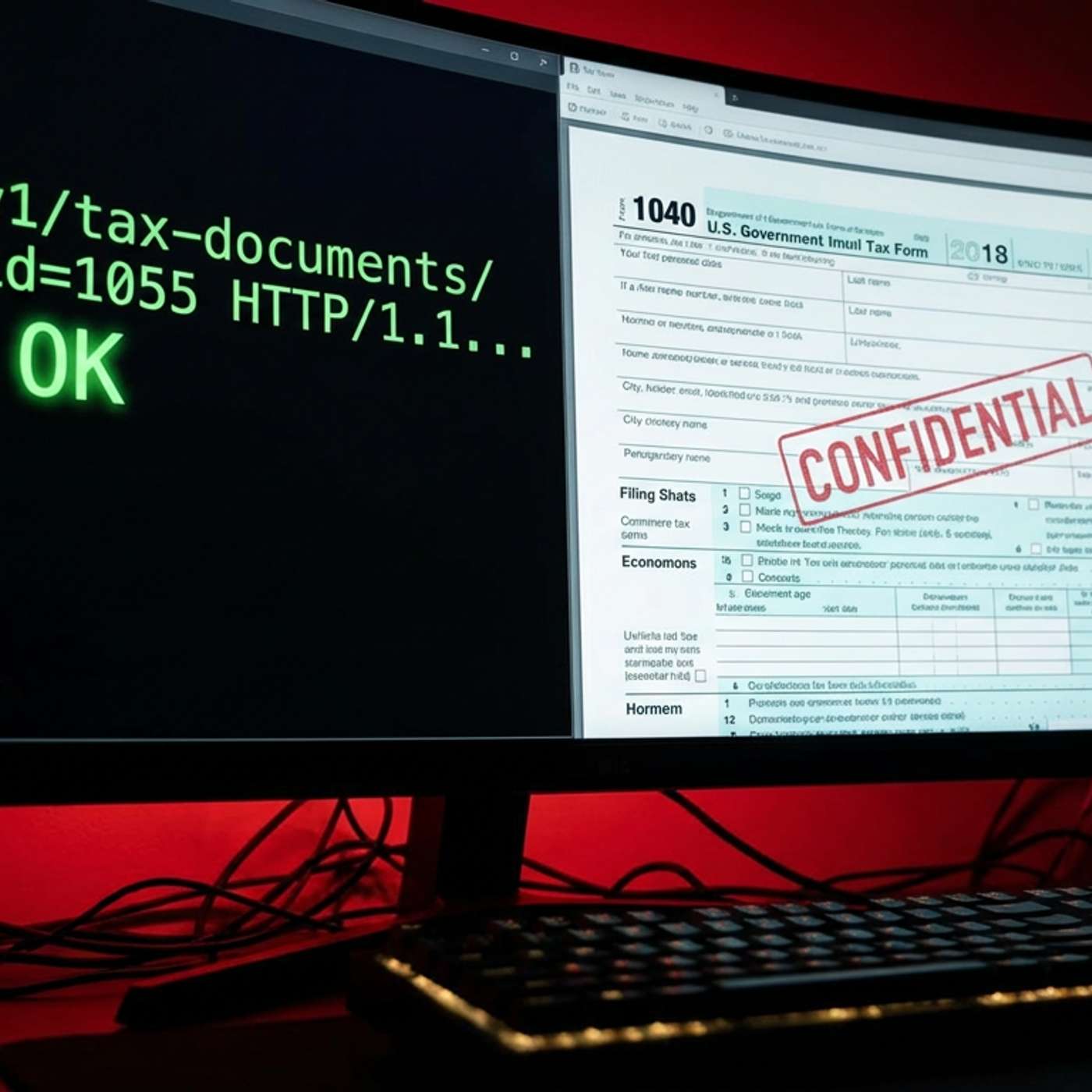
This story was originally published on HackerNoon at: https://hackernoon.com/the-zero-day-deduction.
A bug bounty hunter finds an IDOR vuln in a major tax portal, exposing millions of financial records. A story about privacy, ethics, and the HTTP protocol.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #bug-bounty, #privacy, #web-development, #hacking, #fiction, #contest-tags, #api-bug-bounty, and more.
This story was written by: @legit. Learn more about this writer by checking @legit's about page,
and for more stories, please visit hackernoon.com.
While testing a tax software API for a bug bounty, I discovered a critical Insecure Direct Object Reference (IDOR). By changing a single integer in the URL, I bypassed authentication and accessed a stranger's full tax return. I realized I was one script away from downloading the entire country's financial data.
This story was originally published on HackerNoon at: https://hackernoon.com/inside-the-passwordless-architecture-redefining-security-for-telecom-giants.
Passwordless identity is redefining telecom security by replacing fragile credentials with resilient, cryptographic access built for national scale.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cryptographic-identity-control, #passwordless-telecom-identity, #oss-bss-identity-integration, #workforce-identity-at-scale, #telecom-access-resilience, #passwordless-critical-networks, #large-scale-access-control, #good-company, and more.
This story was written by: @sanya_kapoor. Learn more about this writer by checking @sanya_kapoor's about page,
and for more stories, please visit hackernoon.com.
Passwords were never designed for telecom environments operating at national scale. This article explores how passwordless identity architectures—built as core infrastructure rather than login tools—solve long-standing issues around availability, legacy system integration, Zero Trust alignment, and operational resilience. At telecom scale, identity becomes a control plane, not a credential.
This story was originally published on HackerNoon at: https://hackernoon.com/third-party-risks-in-2026-outlook-and-security-strategies.
Third-party risk is everywhere in 2026. Here's an overview of current risks and security best practices as we start the new year.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #third-party-risk-management, #vendor-risk-management, #vendor-security, #cyber-resilience, #zero-trust, #security-culture, #incident-response-plan, #third-party-risks, and more.
This story was written by: @zacamos. Learn more about this writer by checking @zacamos's about page,
and for more stories, please visit hackernoon.com.
Most companies rely on external services to keep their operations running smoothly, leaving lots of openings for third-party breaches. To create a resilient TPRM program in 2026, companies should embrace automation and AI, foster a culture of security, adopt a zero-trust approach, and more.
This story was originally published on HackerNoon at: https://hackernoon.com/cybersecurity-for-startups-the-assumptions-that-quietly-break-you.
Most startups don’t get hacked due to missing tools, but dangerous assumptions. A founder’s view on how security quietly breaks early-stage startups.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #startups, #software-development, #apis, #leadership, #cybersecurity-for-startups, #startup, #cybersecurity-patterns, and more.
This story was written by: @hakemalhumaidi. Learn more about this writer by checking @hakemalhumaidi's about page,
and for more stories, please visit hackernoon.com.
Startups rarely get compromised because of advanced attacks. They get exposed because of assumptions that feel reasonable under pressure—being too small to matter, trusting encryption blindly, or postponing security decisions. Cybersecurity isn’t a tool problem; it’s a mindset problem. The earlier founders challenge their assumptions, the cheaper—and more effective—security becomes.
This story was originally published on HackerNoon at: https://hackernoon.com/protect-your-crypto-the-wallet-backup-options-you-never-considered.
Ever wondered if your wallet backup is enough? Here’s a friendly rundown of simple tricks and tools that make recovery easier and your crypto far safer.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #crypto-wallet-security, #private-keys, #blockchain-backups, #data-backup, #hardware-wallet-security, #crypto-wallet-backup, #good-company, #obyte, and more.
This story was written by: @obyte. Learn more about this writer by checking @obyte's about page,
and for more stories, please visit hackernoon.com.
With crypto, you’re the only person who has control of your private keys. Because of this, it's helpful to know which backup options are available before losing access to your digital wallet. Hardware wallets can provide an additional level of security.
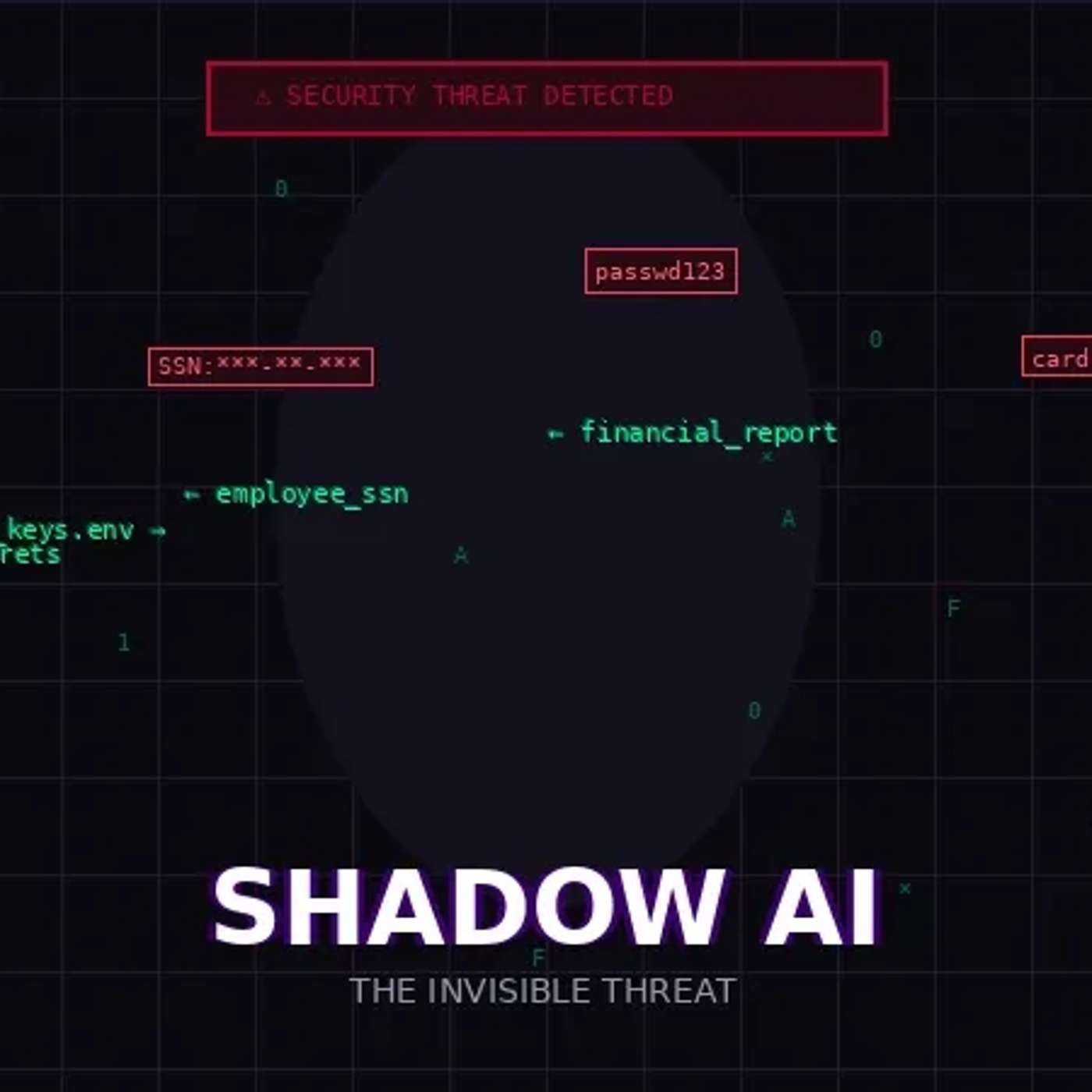
This story was originally published on HackerNoon at: https://hackernoon.com/shadow-ai-the-invisible-threat-lurking-in-your-enterprise.
Shadow AI costs enterprises $670,000 per breach.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #enterprise-security, #shadow-ai, #ai-governance, #cybersecurity, #data-privacy, #zero-trust, #generative-ai, #ai-cybersecurity, and more.
This story was written by: @anjali002. Learn more about this writer by checking @anjali002's about page,
and for more stories, please visit hackernoon.com.
Shadow AI is the unauthorized use of AI tools by employees without IT oversight.
This story was originally published on HackerNoon at: https://hackernoon.com/implementing-zero-trust-cybersecurity-architecture-in-the-age-of-ai.
Explore how Zero Trust secures agentic AI, treating autonomous agents as human actors to prevent misconfigurations, data leaks, and AI-driven breaches.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #ai-agents, #workflow-automation, #zero-trust-security, #ai-innovation, #zero-trust-cybersecurity, #cybersecurity-architecture, #agentic-ai, and more.
This story was written by: @atishkdash. Learn more about this writer by checking @atishkdash's about page,
and for more stories, please visit hackernoon.com.
Agentic AI systems act autonomously across enterprise environments, making traditional perimeter-based security ineffective. Zero Trust treats AI agents as independent actors with identities, enforcing continuous verification, least-privilege access, and contextual controls across APIs, systems, and data. While powerful, Zero Trust must be implemented thoughtfully to avoid policy sprawl, blind spots, and legacy gaps. When done right, it enables organizations to scale autonomous AI safely—without sacrificing speed, innovation, or trust.