Discover whereisyourdata
whereisyourdata

19 Episodes
Reverse
A video guide on how to trace a hotmail
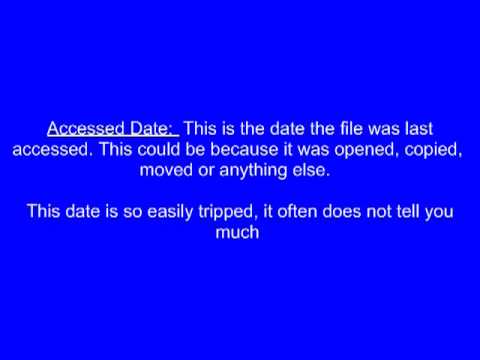
Files can have many dates, the first 4 dates for a file (in the MFT) are shown in this video. Looking at the $Standard_Information Attribute within the MFT.
The examination is conducted using EnCase. These dates are important for those conducting forensic examinations
Computer Forensics - What happens when a file is deleted?
How to use WikiLeaks secure site.
What happens when a drive is wiped? Can the data be recovered? What can computer forensics find? This short video looks at a wiped hard drive with EnCase
Using the popular computer forensics tool, FTK 1.x to keyword search a small set of data.
How to open an EnCase E01 File
Open, working, hard disk drive running inside a glass bell jar... with data activity speed LED's!
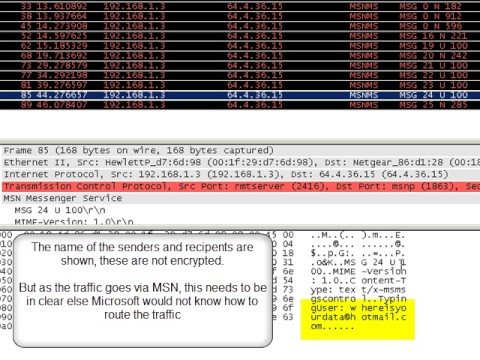
Can you secure MSN? Does the encryption work?
Is it possibly to have a private conversation on a public network? Is MSN secure, if not can it be made secure?
An introduction to "Tor".
Tor is well known for hiding/anonymising IP addresses, but does it work, and can it be used?
Viewing resident and non resident data (i.e data within the MFT) with EnCase
Recovering a deleted file with Encase, from an NTFS formatted USB drive
Demonstrating File slack with with EnCase. File slack can, sometimes, contain information relevant to a case. Even if it does not its important for computer forensics examiners to understand the difference between active files, deleted files, and slack hits.
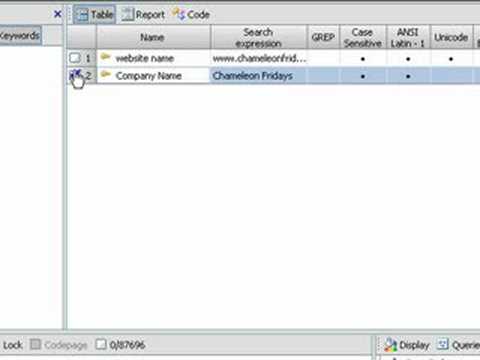
Very basic keyword searching guide for EnCase users
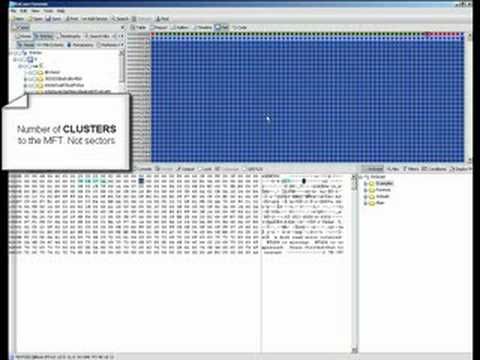
Manually locating the MFT and MFT Mirror from the Volume Boot, using EnCase
Locating the first partition, manually, using Encase
Examining the MBR with EnCase, to locate and identify the partition information