The fakeobj() Primitive: Turning an Address Leak into a Memory Corruption
Update: 2019-06-23
Description
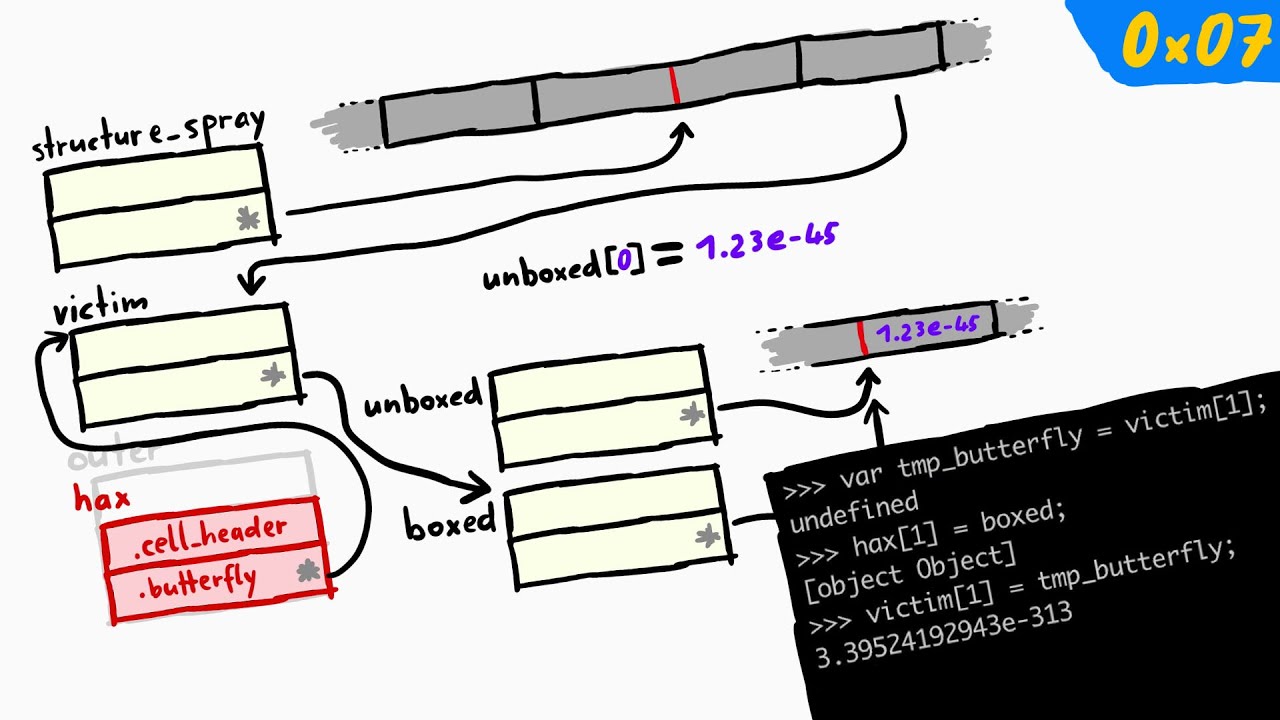
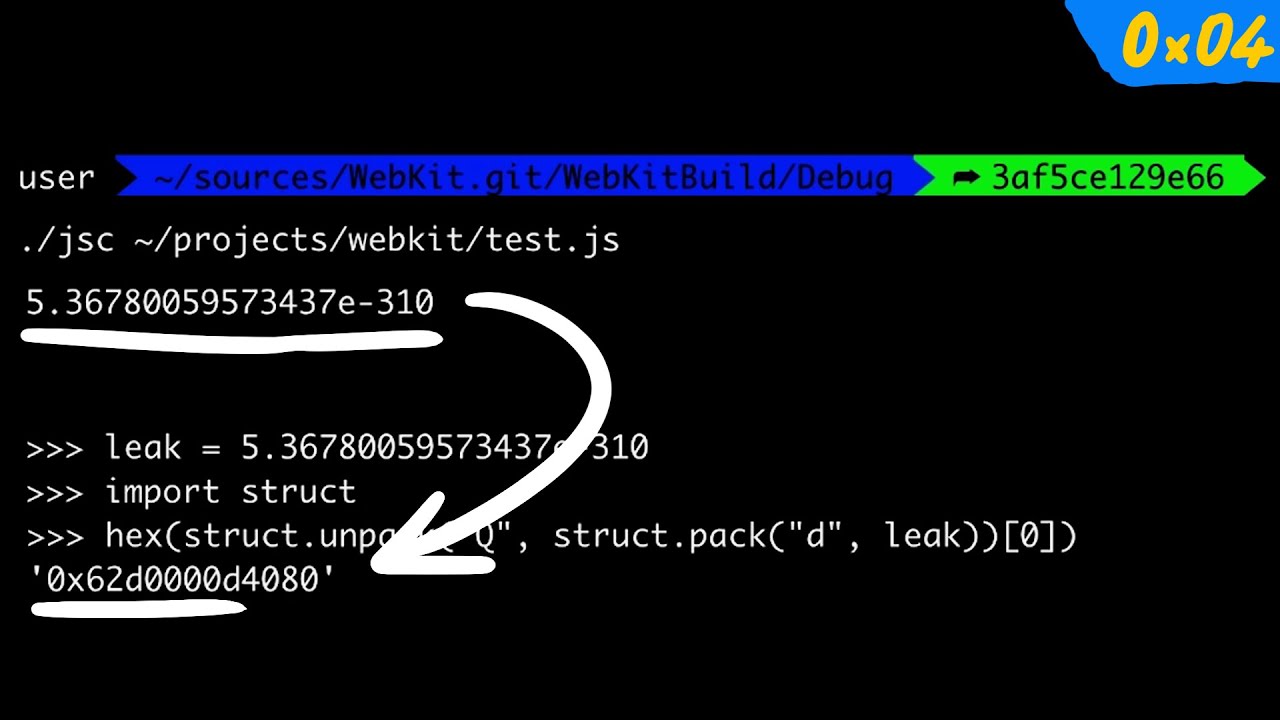
Part5: In this video we turn the bug used in addrof() to corrupt the memory of internal JavaScriptCore Objects which can help us to compromise the engine.
The Exploit: https://github.com/LinusHenze/WebKit-RegEx-Exploit
Saelo's exploit: https://github.com/saelo/cve-2018-4233/blob/master/pwn.js
Saelo's phrack paper: http://www.phrack.org/papers/attacking_javascript_engines.html
-=[ 🔴 Stuff I use ]=-
→ Microphone:* https://amzn.to/2LW6ldx
→ Graphics tablet:* https://amzn.to/2C8djYj
→ Camera#1 for streaming:* https://amzn.to/2SJ66VM
→ Lens for streaming:* https://amzn.to/2CdG31I
→ Connect Camera#1 to PC:* https://amzn.to/2VDRhWj
→ Camera#2 for electronics:* https://amzn.to/2LWxehv
→ Lens for macro shots:* https://amzn.to/2C5tXrw
→ Keyboard:* https://amzn.to/2LZgCFD
→ Headphones:* https://amzn.to/2M2KhxW
-=[ ❤️ Support ]=-
→ per Video: https://www.patreon.com/join/liveoverflow
→ per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join
-=[ 🐕 Social ]=-
→ Twitter: https://twitter.com/LiveOverflow/
→ Website: https://liveoverflow.com/
→ Subreddit: https://www.reddit.com/r/LiveOverflow/
→ Facebook: https://www.facebook.com/LiveOverflow/
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#BrowserExploitation
The Exploit: https://github.com/LinusHenze/WebKit-RegEx-Exploit
Saelo's exploit: https://github.com/saelo/cve-2018-4233/blob/master/pwn.js
Saelo's phrack paper: http://www.phrack.org/papers/attacking_javascript_engines.html
-=[ 🔴 Stuff I use ]=-
→ Microphone:* https://amzn.to/2LW6ldx
→ Graphics tablet:* https://amzn.to/2C8djYj
→ Camera#1 for streaming:* https://amzn.to/2SJ66VM
→ Lens for streaming:* https://amzn.to/2CdG31I
→ Connect Camera#1 to PC:* https://amzn.to/2VDRhWj
→ Camera#2 for electronics:* https://amzn.to/2LWxehv
→ Lens for macro shots:* https://amzn.to/2C5tXrw
→ Keyboard:* https://amzn.to/2LZgCFD
→ Headphones:* https://amzn.to/2M2KhxW
-=[ ❤️ Support ]=-
→ per Video: https://www.patreon.com/join/liveoverflow
→ per Month: https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w/join
-=[ 🐕 Social ]=-
→ Twitter: https://twitter.com/LiveOverflow/
→ Website: https://liveoverflow.com/
→ Subreddit: https://www.reddit.com/r/LiveOverflow/
→ Facebook: https://www.facebook.com/LiveOverflow/
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#BrowserExploitation
Comments
In Channel