Top 4 FIU Case Studies: How Financial Crime Units Combat Cybercrime & Crypto Fraud
Description
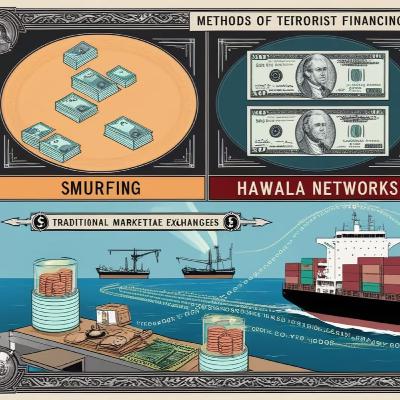
In this episode of FinCrime Jobs, we dive into four landmark FIU case studies that showcase how Financial Intelligence Units around the world are stepping up to tackle increasingly sophisticated cybercrime and cryptocurrency fraud. As digital assets surge in popularity, fraudsters exploit anonymity, decentralized exchanges, and darknet markets—forcing FIUs to innovate new detection and enforcement protocols. Join us as we unpack these real-world investigations, extract best practices, and explore what compliance professionals can learn to safeguard their organizations.
1. The Crypto Mixer Takedown (EU FIU)
Our first case study examines a major joint operation led by an EU member-state FIU to dismantle a notorious cryptocurrency mixing service. By analyzing on-chain transactions, FIU analysts traced obfuscated Bitcoin flows from darknet marketplaces to real-world cash-outs. Leveraging advanced blockchain analytics and international intelligence sharing, the FIU identified the ring’s core operators, froze millions of euros worth of mixed assets, and prosecuted key facilitators under money laundering and cybercrime statutes. This operation underscores the power of combining blockchain forensics with cross-border cooperation.
Key takeaways:
Use clustering algorithms to link mixer addresses to known illicit wallets
File Suspicious Activity Reports (SARs) enriched with on-chain evidence
Coordinate with Europol and other FIUs for asset freezes and arrests
2. Phishing-to-Crypto Fraud (FIU-IND, India)
Next, we highlight India’s FIU-IND investigation into a sophisticated phishing campaign that siphoned user credentials and drained wallets on multiple crypto exchanges. FIU-IND analysts discovered anomalous fund flows from high-risk IP geolocations to off-shore virtual asset service providers (VASPs). Through rapid dissemination of threat indicators to local banks and exchanges—and partnering with CERT-IN—the FIU enabled real-time blocking of suspicious accounts, recovery of a portion of stolen assets, and arrests of the cyber gang behind the scheme.
Key takeaways:
Integrate cyber-intelligence feeds with transaction monitoring
Engage with VASPs for KYC/AML compliance and rapid freeze protocols
Public-private partnerships accelerate incident response
3. Ransomware Payments Tracking (FinCEN, USA)
Our third study explores how FinCEN collaborated with the FBI to trace ransomware payments made in Monero and Bitcoin. By deploying specialized de-mixing tools and soliciting subpoenas for centralized exchange records, investigators followed ransom flows from victim-to-attacker wallets. This led to indictments under the Computer Fraud and Abuse Act and unprecedented cooperation agreements with major crypto custodians. The operation highlighted the necessity of regulatory clarity around privacy coins and the importance of enforcing the FATF Travel Rule for VASPs.
Key takeaways:
Advocate for comprehensive VASP licensing and Travel Rule implementation
Employ advanced heuristics to detect privacy-coin transactions
Leverage legal requests to compel KYC data disclosure
4. Darknet Marketplace Disruption (UK NCA)Finally, we examine the UK’s National Crime Agency (NCA) crackdown on a leading darknet marketplace facilitating crypto-facilitated trafficking. Through targeted undercover buys and on-chain monitoring, the NCA harvested key seller and buyer addresses. FIU analysts then mapped out the ecosystem of associated shell companies and payment processors, resulting in coordinated raids across multiple jurisdictions. The NCA’s strategic use of Suspicious Transaction Reports and Suspicious Activity Reports to alert global partners set a new benchmark for darknet enforcement.Key takeaways:
Conduct hypothesis-driven investigations combining cyber and financial intelligence
Use undercover operations to identify cryptocurrency wallet owners
Synchronize simultaneous takedowns with INTERPOL to prevent asset flight