Discover Cybersecurity Tech Brief By HackerNoon
Cybersecurity Tech Brief By HackerNoon

279 Episodes
Reverse
This story was originally published on HackerNoon at: https://hackernoon.com/why-one-lock-isnt-enough-how-buburuza-designs-multi-layer-security-for-ai-banking.
Why AI banking needs multi-layer security, not just encryption. Buburuza’s COO explains how to stop deepfake fraud and breaches.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #ai-banking-security, #deepfake-fraud, #ai-enabled-cyber-threats, #banking-risk-management, #buburuza-ai-bank, #multi-agentic-security, #financial-fraud-prevention, #good-company, and more.
This story was written by: @sanya_kapoor. Learn more about this writer by checking @sanya_kapoor's about page,
and for more stories, please visit hackernoon.com.
Buburuza COO Grygoriy Bakalor explains why AI banking security must go beyond single-layer encryption. With deepfake fraud surging and breaches eroding trust, banks need multi-layer, multi-agentic defenses that isolate threats, prevent insider risk, and protect users even from mistakes—delivering security that works invisibly but decisively when needed.
This story was originally published on HackerNoon at: https://hackernoon.com/the-hidden-cost-of-invalid-traffic-why-ip-data-is-the-missing-link.
IPinfo stops invalid traffic by detecting bots, VPNs, and proxies with real-time IP intelligence, helping ad platforms cut waste and improve ROI.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #ip-address-intelligence, #ip-data-for-adtech, #invalid-traffic-detection, #residential-proxy-detection, #digital-advertising-accuracy, #bot-traffic-mitigation, #advertising-fraud-prevention, #good-company, and more.
This story was written by: @ipinfo. Learn more about this writer by checking @ipinfo's about page,
and for more stories, please visit hackernoon.com.
Invalid traffic (IVT) is draining billions from advertising budgets as bots, VPNs, and residential proxies distort CPMs, attribution, and ROI. IPinfo prevents these losses by identifying non-human traffic at the IP level using continuously validated, measurement-based IP intelligence. With real-time proxy/VPN detection, active IPv6/IPv4 validation, and high-accuracy enrichment, platforms can block IVT before it enters auctions—leading to cleaner supply, better performance, and stronger ROI.
This story was originally published on HackerNoon at: https://hackernoon.com/the-battle-for-the-borders-how-ai-and-cyber-intelligence-are-reshaping-statecraft.
From Tel Aviv to Silicon Valley, a new generation of AI-driven intelligence platforms is redefining how states secure their borders.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #ai, #cyber-intelligence, #state-cybersecurity, #palantir, #babel, #fivecast, #good-company, and more.
This story was written by: @nicafurs. Learn more about this writer by checking @nicafurs's about page,
and for more stories, please visit hackernoon.com.
From Tel Aviv to Silicon Valley, a new generation of AI-driven intelligence platforms is redefining how states secure their borders.
This story was originally published on HackerNoon at: https://hackernoon.com/link11-identifies-five-cybersecurity-trends-set-to-shape-european-defense-strategies-in-2026.
DDoS attacks will increasingly be used as Diversion Tactics. API-First Architectures Increase Exposure to Misconfigurations and Business Logic Abuse.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #link11, #cybernewswire, #press-release, #link11-announcement, #blockchain-development, #crypto-exchange, #good-company, and more.
This story was written by: @cybernewswire. Learn more about this writer by checking @cybernewswire's about page,
and for more stories, please visit hackernoon.com.
Link11 has identified five developments expected to define the cybersecurity environment for European organizations in the year ahead. DDoS attacks will increasingly be used as Diversion Tactics. API-First Architectures Increase Exposure to Misconfigurations and Business Logic Abuse.
This story was originally published on HackerNoon at: https://hackernoon.com/debunking-the-998percent-accurate-ip-data-claim.
IPinfo explains why ‘99% accurate IP data’ is misleading and how real accuracy requires ongoing measurement, transparency, and ProbeNet validation.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #ip-data-accuracy, #ip-geolocation-accuracy, #ipinfo-probenet, #ip-intelligence-reliability, #ip-address-verification, #ip-data-measurement, #ipv4-ipv6-data-validation, #good-company, and more.
This story was written by: @ipinfo. Learn more about this writer by checking @ipinfo's about page,
and for more stories, please visit hackernoon.com.
Most “99%+ accurate” IP geolocation claims are misleading because there’s no shared dataset, no standard methodology, and no way to validate global accuracy across billions of constantly changing IPs. IPinfo rejects the industry’s accuracy theater and instead uses continuous measurement, transparency, and real-world validation to deliver trustworthy, evidence-backed IP data accuracy.
This story was originally published on HackerNoon at: https://hackernoon.com/what-i-learned-from-scanning-dozens-of-small-government-websites-and-why-the-same-bugs-keep-coming.
What I found while scanning dozens of small U.S. government websites with an open-source tool — the same five security mistakes and how to fix them.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #web-security, #cybersecurity, #govtech-user-experience, #govtech, #opensource, #webdev, #devops, #legacy-cms, and more.
This story was written by: @civicmeshflow. Learn more about this writer by checking @civicmeshflow's about page,
and for more stories, please visit hackernoon.com.
I built an open-source scanner and pointed it at small U.S. government websites. The same five security mistakes kept showing up: weak HTTPS, no CSP, leaky test files, insecure cookies and outdated JS – plus a simple baseline to fix them.
This story was originally published on HackerNoon at: https://hackernoon.com/sase-meets-edge-ai-why-security-will-be-decided-in-the-first-millisecond.
In security, milliseconds decide trust. Why Edge AI must judge every packet instantly to prevent threats without killing performance.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #zero-trust-network-accesss, #edge-ai, #sase, #network-security, #enterprise-ai-infrastructure, #cyber-resilience, #latency-optimization, #cloud-native-security, and more.
This story was written by: @dhavalpowar. Learn more about this writer by checking @dhavalpowar's about page,
and for more stories, please visit hackernoon.com.
Enterprise security is shifting to the edge, where the first millisecond of every connection determines trust, performance, and risk. Traditional SASE cannot keep pace with encrypted traffic, global latency, and attacker speed. Edge AI changes the model by making sub-millisecond, context-aware decisions directly at ingress, turning security into an instantaneous, distributed judgment system.
This story was originally published on HackerNoon at: https://hackernoon.com/the-hidden-cost-of-free-apps-and-the-battle-for-your-attention.
The “free” model of popular apps often disguises data collection, behavioral profiling, and monetization of user attention.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity-awareness, #apps, #free-apps, #targeted-ads, #affiliate-marketing, #data-resale, #hidden-cost-of-ads, #psychology-in-app-development, and more.
This story was written by: @mark-smith. Learn more about this writer by checking @mark-smith's about page,
and for more stories, please visit hackernoon.com.
The “free” model of popular apps often disguises data collection, behavioral profiling, and monetization of user attention. Features like infinite scroll, autoplay, and push notifications aren't about convenience; they’re designed to override your natural stopping cues. Regaining control over attention requires conscious digital habits, platform accountability, and greater public awareness of manipulative design.
This story was originally published on HackerNoon at: https://hackernoon.com/is-shadow-ai-worse-than-shadow-it.
Shadow IT was just the first of the hidden threats; now shadow AI has upped the ante. But which is worse — and how can you defend against them?
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #ai-security, #shadow-it, #shadow-ai, #shadow-ai-risks, #shadow-it-detection, #ai-governance, #ai-in-business, #cybersecurity, and more.
This story was written by: @zacamos. Learn more about this writer by checking @zacamos's about page,
and for more stories, please visit hackernoon.com.
An extension of shadow IT, shadow AI involves employees using non-approved AI technology. Security teams can reduce shadow AI exposure by building a clear AI governance framework, provide approved AI tools, and more.
This story was originally published on HackerNoon at: https://hackernoon.com/authorization-in-the-age-of-ai-agents-beyond-all-or-nothing-access-control.
Authorization is the process of determining *what* you’re allowed to do.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #ai-security, #artificial-intelligence, #ai-agents, #machine-learning, #ai-agents-authorization, #ai-authorization, #role-based-access-control, and more.
This story was written by: @lab42ai. Learn more about this writer by checking @lab42ai's about page,
and for more stories, please visit hackernoon.com.
Authorization is the process of determining *what* you’re allowed to do. It’s the invisible security perimeter around every digital interaction you have. If authorization fails, everything fails.
This story was originally published on HackerNoon at: https://hackernoon.com/automating-incident-response-how-to-reduce-malware-forensics-time-by-99percent-with-python-and-virustotal.
Build a pipeline that aggressively removes "Safe" files using three layers.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #digital-forensics, #malware, #incident-response, #security, #nist, #virus-total, #cybersecurity-funnel, #cysec-funnel-architecture, and more.
This story was written by: @dippusingh. Learn more about this writer by checking @dippusingh's about page,
and for more stories, please visit hackernoon.com.
The average time to resolve a cyber incident is 43 days. Manually analyzing 5,000 files takes 80 hours. We will build a pipeline that aggressively removes "Safe" files using three layers.
This story was originally published on HackerNoon at: https://hackernoon.com/the-sudo-problem-why-google-is-locking-down-ai-agents-before-they-break-the-web.
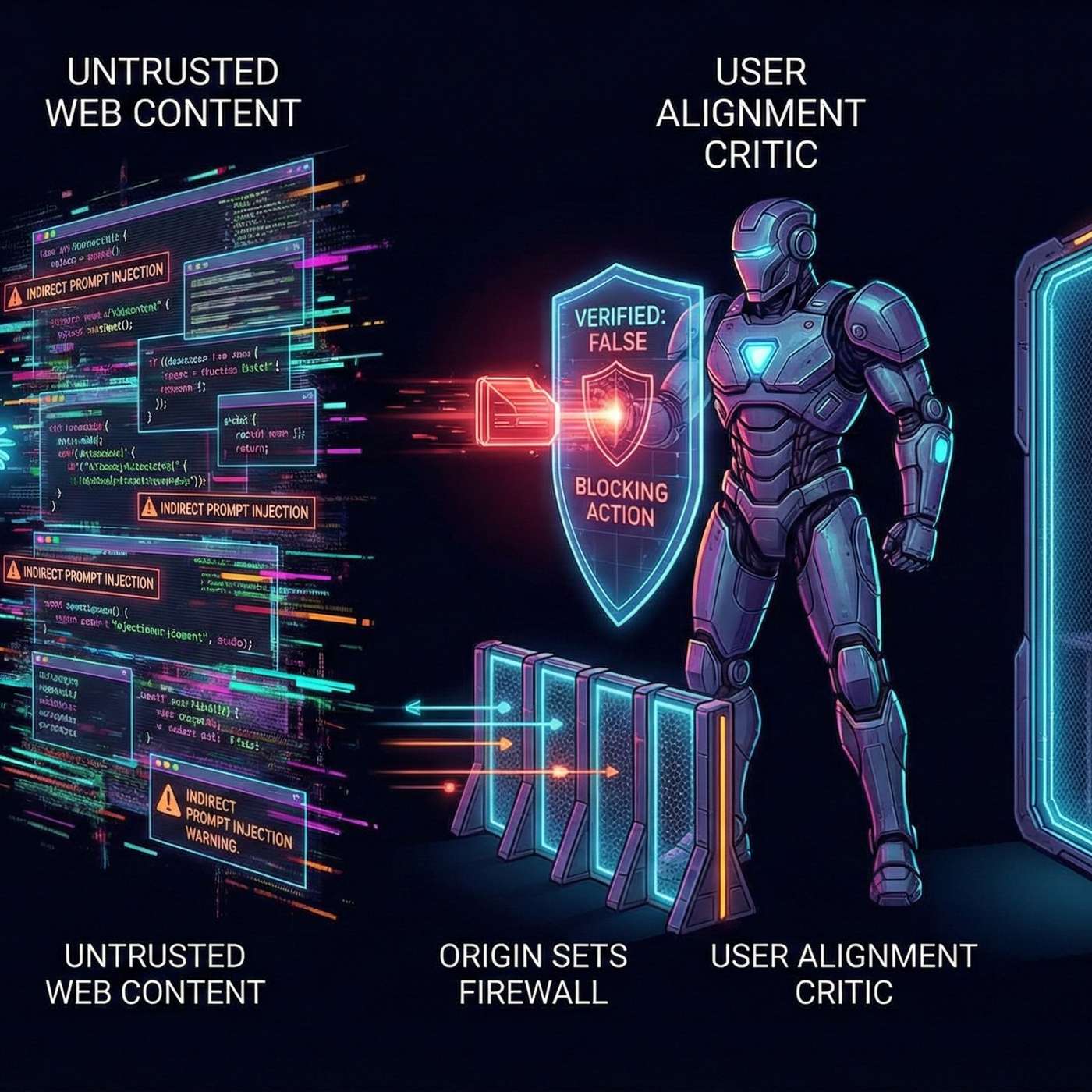
Google has released a whitepaper on how they are architecting security for Chrome’s new Agentic capabilities.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #ai-agents, #artificial-intelligence, #web-security, #google, #ai-web, #indirect-prompt-injection, #user-alignment-critic, and more.
This story was written by: @aiguru. Learn more about this writer by checking @aiguru's about page,
and for more stories, please visit hackernoon.com.
Google has released a whitepaper on how they are architecting security for Chrome’s new Agentic capabilities.
This story was originally published on HackerNoon at: https://hackernoon.com/ine-earns-g2-winter-2026-badges-across-global-markets.
Awards include Leader status in the Online Course Providers Grid Report, Momentum Leader recognition in two major training categories, and regional leadership.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #ine-security, #cybernewswire, #press-release, #ine-security-announcement, #cyber-threats, #cyber-security-awareness, #good-company, and more.
This story was written by: @cybernewswire. Learn more about this writer by checking @cybernewswire's about page,
and for more stories, please visit hackernoon.com.
INE has been recognized with seven G2 Winter 2026 badges. Awards include Leader status in the Online Course Providers Grid Report, Momentum Leader recognition in two major training categories, and regional leadership.
This story was originally published on HackerNoon at: https://hackernoon.com/the-louvre-heist-intimidation-dna-and-the-real-story-behind-the-global-headline.
Louvre heist and how the simple password is not the story.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #cyber-threats, #louvre-heist, #password-security, #password-protection, #louvre-password, #louvre-theft, #museum-robbery, and more.
This story was written by: @blackheart. Learn more about this writer by checking @blackheart's about page,
and for more stories, please visit hackernoon.com.
The Louvre Museum is the world's largest art museum by exhibition space. The museum holds over 550,000 objects in total, with the majority kept in climate-controlled storage facilities for preservation. The public display area is vast, covering roughly 73,000 m², where about 35,000 works of art are on display.
This story was originally published on HackerNoon at: https://hackernoon.com/i-built-a-tiny-browser-only-encryption-tool-because-i-dont-trust-your-backend.
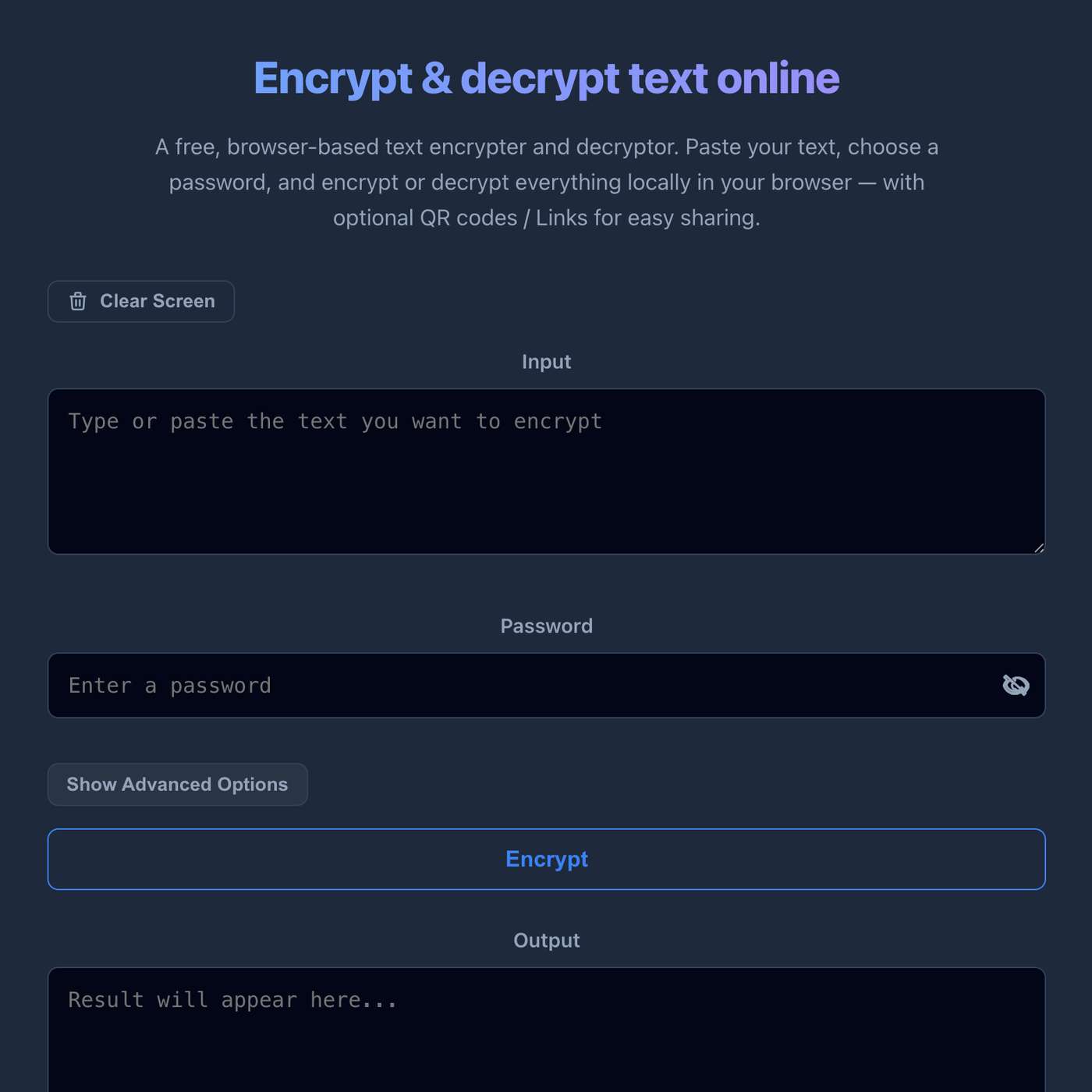
A developer builds Encrypter, a browser-only tool for encrypting text without servers, logins, or tracking—offering a simple, secure way to share secrets.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #encryption, #web-security, #client-side-encryption, #web-crypto-api, #aes-gcm-encryption, #static-site-security, #password-based-encryption, #data-privacy-tools, and more.
This story was written by: @raulsingapore. Learn more about this writer by checking @raulsingapore's about page,
and for more stories, please visit hackernoon.com.
I built Encrypter, a static browser-only text encryption tool that turns secrets into shareable ciphertext (links/QR), keeps crypto in the Web Crypto API, and never sends your plaintext to a server.
This story was originally published on HackerNoon at: https://hackernoon.com/securing-kafka-for-pci-dss-compliance-a-practical-guide-for-financial-data-pipelines.
comprehensive guide on aligning Kafka security with PCI DSS requirements, covering topics like Encryption, authentication and access Control, Auditing and monit
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #data-security, #secure-data-pipelines, #kafka-security, #pci-dss-compliance, #data-encryption-kafka, #kafka-authentication, #financial-data-protection, #secure-data-streaming, and more.
This story was written by: @iamanant. Learn more about this writer by checking @iamanant's about page,
and for more stories, please visit hackernoon.com.
Kafka is a powerful streaming platform capable of handling billions of events. It has a distributed architecture, high throughput, and fault tolerance. Kafka is used to broadcast real-time market data from various sources such as forex markets, and stock exchange.
This story was originally published on HackerNoon at: https://hackernoon.com/how-quantum-computers-threaten-bitcoin-and-the-entire-internet-simply-explained.
Learn how Shor's Algorithm breaks RSA, ECC, and Bitcoin. Understand the 'Decrypt Later' threat and the urgent global race for Post-Quantum Cryptography (PQC).
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #post-quantum-cryptography, #quantum-computing, #shor's-algorithm, #store-now-decrypt-later, #quantum-timeline, #nist, #rsa-ecc-pqc, #sndl, and more.
This story was written by: @thomascherickal. Learn more about this writer by checking @thomascherickal's about page,
and for more stories, please visit hackernoon.com.
Quantum cryptography is a ticking time bomb placed at the foundations of our digital world. The world is in a race to build a new generation of cryptography before the clock strikes zero. Read the full story explained in extremely simple terms for everyone.
This story was originally published on HackerNoon at: https://hackernoon.com/$146-million-in-rwa-hacks-this-year-reveals-the-gap-between-tokenization-hype-and-reality.
RWA tokenization hit $35.68B in 2025, but $14.6M in hacks exposed security gaps. Can the industry scale to $2 trillion by 2028 amid regulatory fragmentation?
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #blockchain-security, #rwa-tokenization, #real-world-assets, #defi-exploits, #cryptocurrency-regulation, #genius-act, #web3-hacks, #web3-breaches, and more.
This story was written by: @johnwrites. Learn more about this writer by checking @johnwrites's about page,
and for more stories, please visit hackernoon.com.
Real-world asset (RWA) tokenization reached $35.68 billion in 2025, with projections to hit $2 trillion by 2028. But the rapid growth exposed critical vulnerabilities: $14.6 million was lost to hacks—more than double the previous year—with most exploits occurring in DeFi wrappers rather than the tokenized assets themselves.
The GENIUS Act provided regulatory clarity for stablecoins but left gaps across the full asset lifecycle. Meanwhile, institutional giants like BlackRock, JPMorgan, and State Street are building on private blockchains, validating the market but creating interoperability challenges.
Platforms like Mavryk (tokenizing $10B in luxury real estate), Ondo Finance (Treasury-backed tokens), and Securitize (infrastructure provider) are attempting to bridge institutional compliance with public blockchain efficiency.
This story was originally published on HackerNoon at: https://hackernoon.com/the-invisible-breach-how-ai-is-quietly-creating-new-security-blind-spots-in-modern-tech.
We're watching organizations introduce sophisticated machine learning systems to reduce risk, only to discover its creating entirely new categories of risk.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #cybersecurity, #ai-cybersecurity, #ai-security-lapse, #ai-security-lapses, #ai-in-cybersecurity, #ai-driven-security, #security-orchestration, #security-orchestration-tool, and more.
This story was written by: @drechimyn. Learn more about this writer by checking @drechimyn's about page,
and for more stories, please visit hackernoon.com.
We're watching organizations introduce sophisticated machine learning systems to reduce risk, only to discover those same systems are creating entirely new categories of vulnerability.
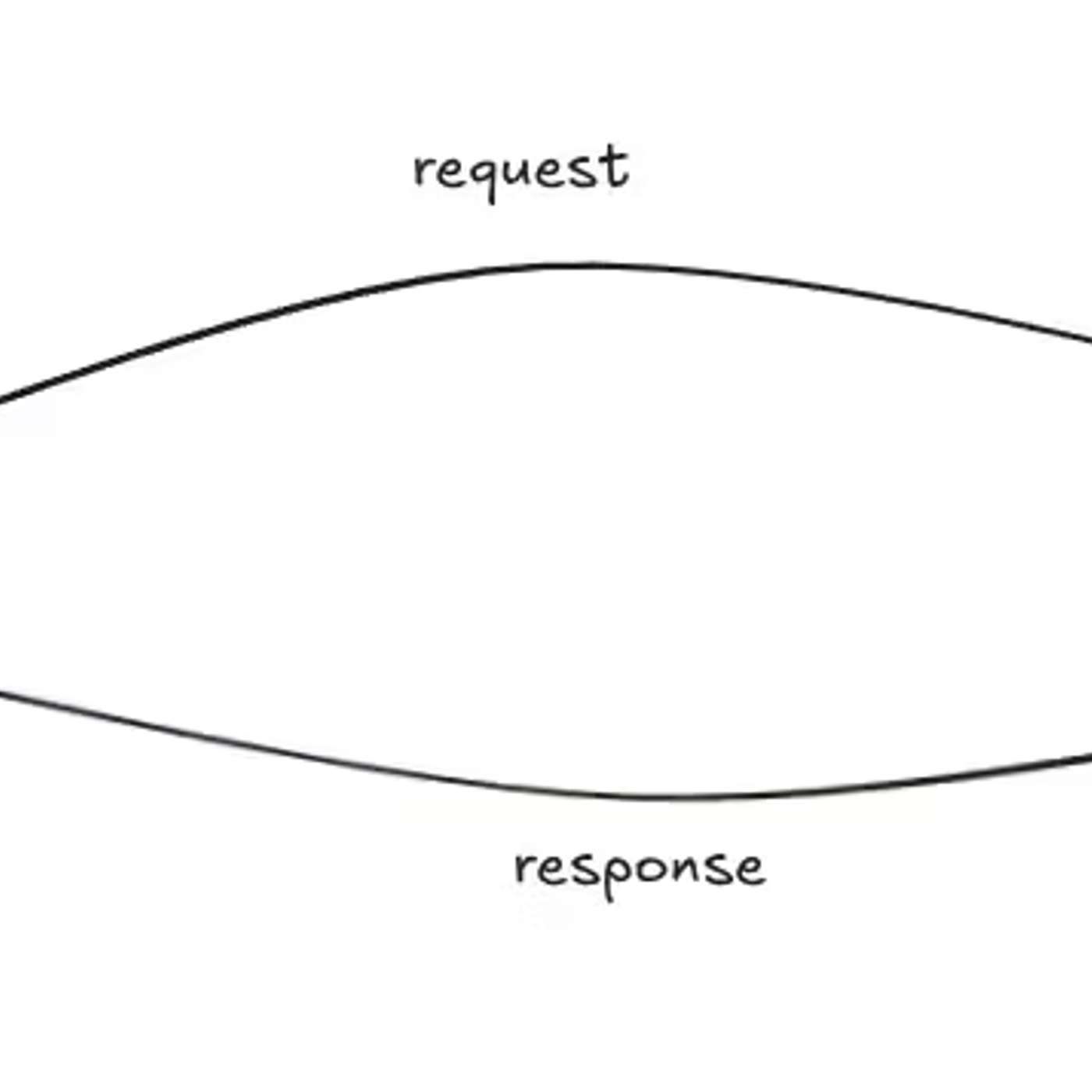
This story was originally published on HackerNoon at: https://hackernoon.com/how-request-response-really-works.
Learn how the request–response model really works under the hood.
Check more stories related to cybersecurity at: https://hackernoon.com/c/cybersecurity.
You can also check exclusive content about #network, #request-response-model, #request-response-pattern, #client-server, #http-request-response, #web-request-response, #web-development-fundamentals, #backend-basics, and more.
This story was written by: @majjikishore. Learn more about this writer by checking @majjikishore's about page,
and for more stories, please visit hackernoon.com.
Learn how the request–response model really works under the hood.