An Attacker Looks at Docker: Approaching Multi-Container Applications
Update: 2018-08-28
Description
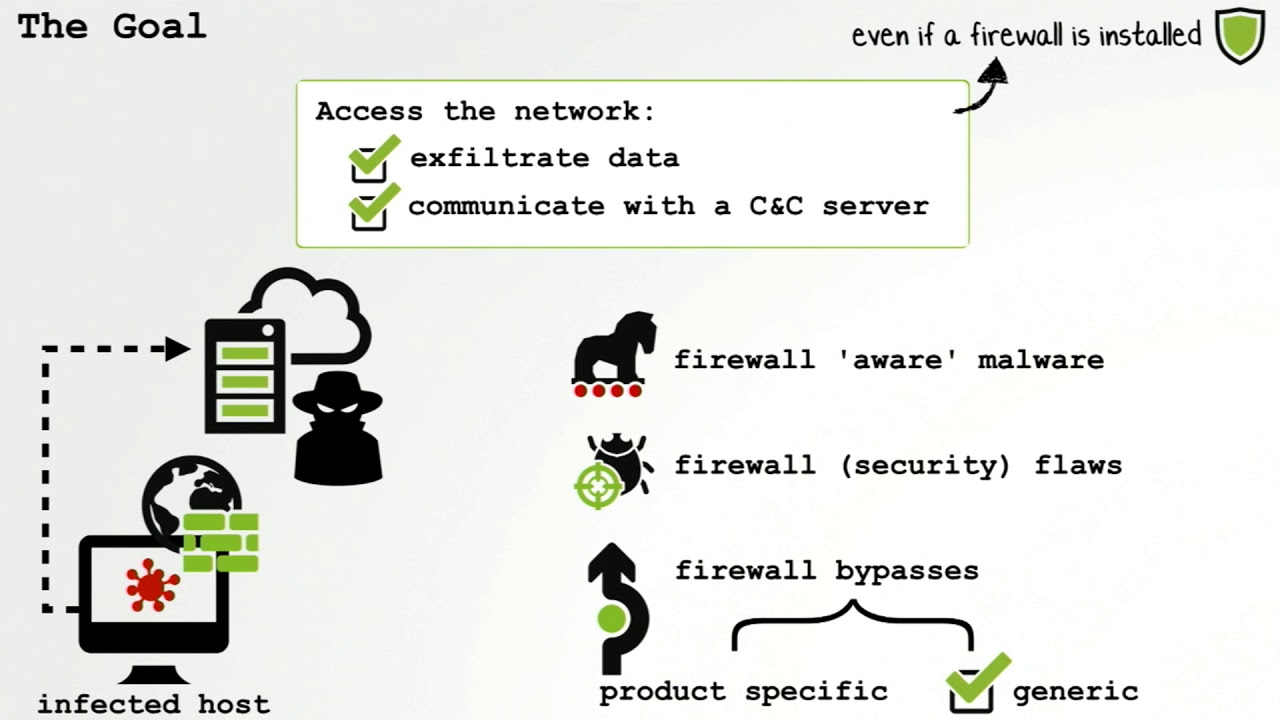
The goal of this talk is to provide a penetration tester experienced in exploitation and post-exploitation of networks and systems with an exposure to containerization and the implications it has on offensive operations.
By Wesley McGrew
Full Abstract & Presentation Materials: https://www.blackhat.com/us-18/briefings/schedule/#an-attacker-looks-at-docker-approaching-multi-container-applications-9975
By Wesley McGrew
Full Abstract & Presentation Materials: https://www.blackhat.com/us-18/briefings/schedule/#an-attacker-looks-at-docker-approaching-multi-container-applications-9975
Comments
In Channel