Unpacking the Packed Unpacker: Reverse Engineering an Android Anti-Analysis Native Library
Update: 2018-08-28
Description
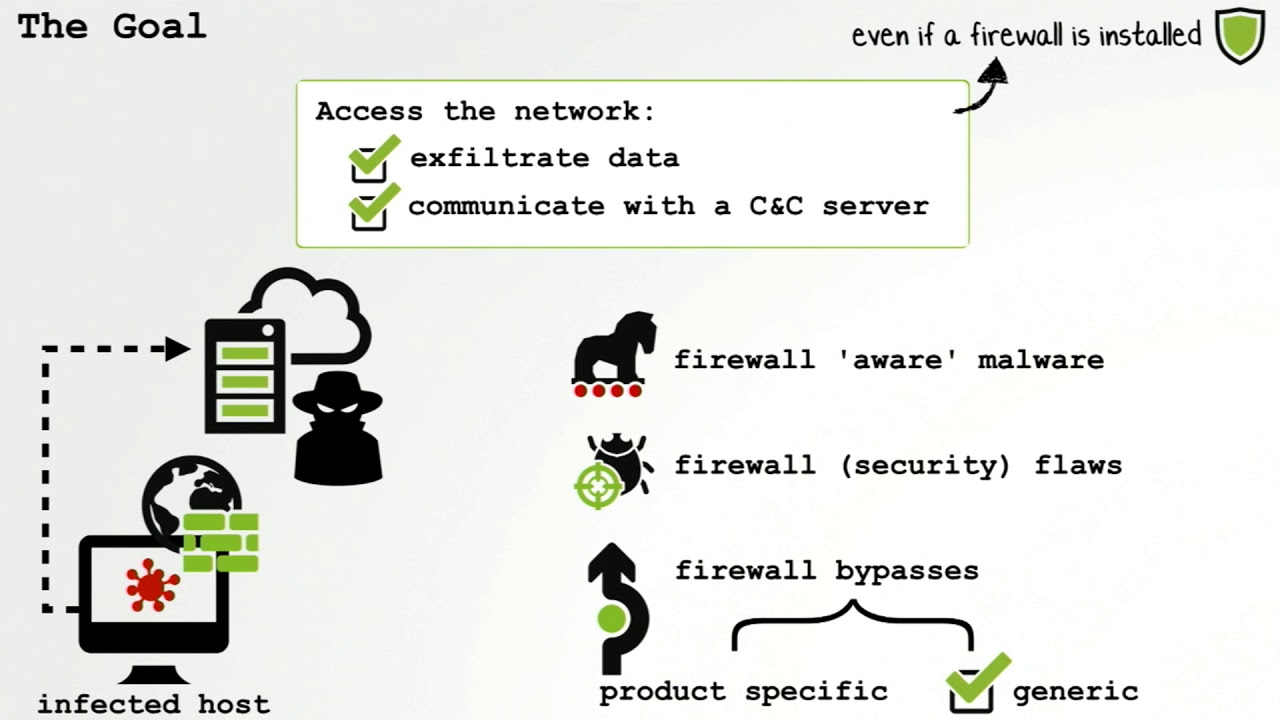
I will discuss each of the techniques the malware author used in order to prevent reverse engineering of their Android native library including manipulating the Java Native Interface, encryption, run-time environment checks, and more. This talk discusses not only the techniques the malware author implemented to prevent analysis, but also the steps and process for a reverse engineer to proceed through the anti-analysis traps.
By Maddie Stone
Full Abstract & Presentation Materials: https://www.blackhat.com/us-18/briefings/schedule/index.html#unpacking-the-packed-unpacker-reverse-engineering-an-android-anti-analysis-native-library-10795
By Maddie Stone
Full Abstract & Presentation Materials: https://www.blackhat.com/us-18/briefings/schedule/index.html#unpacking-the-packed-unpacker-reverse-engineering-an-android-anti-analysis-native-library-10795
Comments
In Channel